So, what exactly is digital asset recovery?
Think of it less like a magic "undo" button and more like a specialized safecracking service for your digital vault. It's the process of getting back into cryptocurrency wallets and other digital tokens you've been locked out of. This isn't just guesswork; it's a mix of deep forensic analysis, cryptographic know-how, and a whole lot of computing power to either crack a forgotten password or pull data from a dead piece of hardware.
The High-Stakes World of Digital Asset Recovery
We’ve all heard the stories—someone finds an old laptop in the attic, remembers it has a crypto wallet on it, but the password is a distant memory. This isn't just a hypothetical situation; it's a reality for a shocking number of people. And as the value of crypto continues to climb, the stakes for getting that access back have never been higher.

What used to be a tiny, niche service has exploded into a crucial part of the digital economy. The sheer amount of money locked away or lost is staggering. We're also seeing a massive shift in how high-profile crypto thefts are handled, with law enforcement becoming increasingly skilled at tracing and clawing back stolen funds.
Just look at the numbers. In 2025 alone, cryptocurrency thefts topped $3.4 billion, and a whopping 69% of the losses from service breaches came from just three major hacks. If you want to dive deeper into these trends, the latest crypto crime reports from Chainalysis are always an eye-opener.
Understanding How Assets Are Lost
Before we get into the "how" of recovery, it's critical to understand the "why." How do people lose access in the first place? The path to a solution depends entirely on what went wrong, and each scenario brings its own unique set of headaches.
Here's a quick look at the most common ways people get locked out of their digital assets.
How Digital Assets Are Typically Lost
This table gives a quick overview of the most common scenarios that lead to the loss of digital assets, highlighting the different challenges each presents for recovery.
| Cause of Loss | Common Example | Recovery Feasibility |
|---|---|---|
| Forgotten Credentials | You can't remember the password for your Bitcoin Core wallet.dat file. |
High. Brute-force attacks are often successful if you remember parts of the password. |
| Hardware Failure | The hard drive holding your Exodus wallet files crashes and won't boot up. | Medium. Depends on the extent of the damage. Data recovery specialists may be needed first. |
| Lost Seed Phrase | Your 12-word recovery phrase for a Ledger hardware wallet is lost or destroyed. | Very Low. Without the seed phrase, the assets are almost always permanently lost. |
| Theft and Scams | You clicked a phishing link and a scammer drained your MetaMask wallet. | Very Low. Recovery relies on law enforcement tracing, which is complex and rare. |
Understanding your specific situation is the first step toward finding a viable recovery path.
At its core, digital asset recovery is a disciplined process. It's about systematically applying specialized knowledge to reconstruct access, whether that means cracking a password or piecing together fragmented data from a failing drive.
This guide will unpack what's really involved in getting your assets back. By understanding the common pitfalls, we can explore practical strategies and, just as importantly, learn how to prevent these situations from happening again. It’s all about giving you a clear path forward, no matter how complex the problem seems.
Why Digital Assets Disappear
Figuring out how your assets went missing is the first, most critical step toward getting them back. It almost always boils down to one of two things: a simple, honest mistake or a targeted attack from the outside.
Think of it this way: a self-inflicted loss is like losing the keys to your own house. It's frustrating, it's on you, but the house is still there, locked and safe. This is, by far, the most common situation we encounter.
An external attack, on the other hand, is like someone stealing those keys through a clever trick. A malicious actor is actively involved, which makes the path to recovery a whole lot more complicated.
Common Self-Inflicted Losses
Human error is the number one reason people get locked out of their crypto. These situations can be absolutely gut-wrenching because the funds are technically still there, just trapped behind a digital wall you can no longer get through.
- Forgotten Passwords: This is the classic. You set a super-secure password for a wallet file (like a Bitcoin Core
wallet.dat) years ago, and now it’s a complete blank. - Lost Seed Phrases: Your seed phrase is the master key to everything. If the piece of paper you wrote it on is lost, destroyed in a flood, or thrown out by accident, you're in trouble unless a backup exists somewhere.
- Hardware Failure: Hard drives die. Laptops give up the ghost. Phones take a swim. If your wallet was only on that single device and you don't have the seed phrase backed up elsewhere, you're suddenly dealing with a data recovery problem on top of a crypto recovery problem.
The good news? These cases are tough, but they're often solvable. A forgotten password can sometimes be brute-forced with enough computing muscle, and data can often be pulled from a damaged drive by forensic specialists. The key is that you still have the device or at least some fuzzy memory of the password to start with.
The Threat of External Attacks
External attacks are a different beast entirely. Your assets aren’t just misplaced; they’ve been actively stolen. And the methods criminals use are getting sneakier and more sophisticated every day.
The sheer scale of these attacks is staggering. We're seeing a major shift away from huge, single exchange hacks. Attackers are now diversifying, targeting individuals in a higher volume of personal wallet compromises. This makes your personal security more critical than ever.
One of the oldest and most effective tricks in the book is phishing. A scammer sends you an email or message that looks legit—like it's from your exchange or wallet provider. They trick you into clicking a bad link and typing in your private keys or seed phrase. Just like that, they have direct access to drain your account.
Another huge threat is malware. Malicious software, like a keylogger, can infect your computer and quietly record every single thing you type, including your wallet passwords. Once the attacker has your credentials, they can log in from anywhere and empty your accounts.
The Rise of Sophisticated Theft
Digital theft isn't just a game for lone-wolf hackers anymore. It's become alarmingly professional, with state-sponsored groups now dominating the field of large-scale attacks.
For instance, detailed analysis reveals that state-linked actors, especially those from the DPRK, have become the main culprits behind major service breaches. In 2025, they were responsible for a shocking 76% of all funds stolen from these platforms. This has pushed the total theft attributed to them to an estimated $6.75 billion since their campaigns kicked off. If you want to dive deeper into these evolving threats, the latest crypto crime reports offer some powerful insights.
Knowing whether your assets were lost to a mistake or stolen in an attack is fundamental. It dictates your entire strategy—whether you should focus on a technical digital asset recovery process like password cracking, or begin the long and difficult road of working with law enforcement to try and trace the stolen funds.
Exploring Your Asset Recovery Options

Once you’ve pinpointed why you can't get to your crypto, the next step is figuring out how to get it back. The world of digital asset recovery isn’t about one-size-fits-all solutions. It’s more like a specialized locksmith’s toolkit—each tool is precision-engineered for a specific type of lock.
Picking the wrong tool won’t just fail to open the lock; it can break it permanently. You wouldn't use a sledgehammer on a fine-tuned safe, and you wouldn't try to pick a rusted-shut padlock with a paperclip. In the same way, the method for recovering your funds depends entirely on the problem at hand.
Brute-Force Attacks for Forgotten Passwords
This is probably the recovery method most people have heard of. It’s the go-to strategy when you've forgotten a wallet password but still have the actual wallet file. A brute-force attack is just what it sounds like: a powerful computer trying millions—or even billions—of password combinations until it lands on the right one.
But it's not just blind guessing. The whole process becomes exponentially more effective if you can feed it clues.
- Password Patterns: Can you remember bits and pieces? A favorite phrase, a specific year, or a character you always used at the end?
- Character Sets: Did you use uppercase letters? Numbers? Symbols like
!or#? - Password Length: Do you have a rough idea of how many characters it was?
Every single clue you can provide drastically shrinks the search area, turning a nearly impossible task into a solvable puzzle. Without any hints, trying to crack a truly random, complex password could take centuries.
A brute-force attack is a numbers game. Its success hinges on the complexity of the original password and the quality of the information you can provide to guide the search. The more you remember, the higher the chance of a successful recovery.
Digital Forensics for Damaged Hardware
But what if the problem isn’t a forgotten password, but a crashed laptop or a corrupted hard drive? This is where digital forensics comes in. It’s a highly specialized field focused on pulling data from storage devices that are dead, damaged, or have been wiped clean.
A forensic expert can often bypass a computer’s fried operating system to get directly at the raw data on the physical memory chips. Their mission is to find and reconstruct the fragmented wallet files or private keys buried deep within that data. This is painstaking work, often requiring a clean-room environment to avoid causing more damage.
The odds of success here depend entirely on the type and extent of the damage. A drive with software errors or one that was accidentally formatted has a pretty good chance of recovery. A drive that’s been shattered or fried in a fire? That's a much tougher challenge.
Cryptographic Analysis for Seed Phrases
Losing a full 12 or 24-word seed phrase is a nightmare, and recovering it from thin air is basically impossible. But what if you have most of it? That's when cryptographic analysis can be a lifesaver.
This method works in scenarios like:
- Words Out of Order: You wrote down all 24 words but have no idea what the correct sequence is.
- One or Two Missing Words: You’ve got 22 of the 24 words, but the last two are just gone.
- Uncertainty About a Word: You can’t remember if a word was "awake" or "aware."
In these situations, specialized software can run through every possible combination based on the information you do have. It systematically tries different word orders or plugs in every possible word from the official BIP39 list to find the one combination that unlocks a valid wallet. When only a few puzzle pieces are missing, this becomes a very solvable computational problem.
Comparing Recovery Methods and Their Uses
To make things clearer, let’s break down which tool is right for which job. Each approach has its own specific requirements and chances of success.
| Recovery Method | Best For | Key Requirement | Success Rate Factor |
|---|---|---|---|
| Brute-Force Attack | Forgotten passwords for wallet files like wallet.dat or JSON keystores. |
The encrypted wallet file and any partial memories of the password. | The complexity of the password and the accuracy of your clues. |
| Digital Forensics | Corrupted, damaged, or otherwise inaccessible hard drives, SSDs, and phones. | The physical storage device (e.g., the hard drive or phone itself). | The physical integrity of the memory chip inside the device. |
| Cryptographic Analysis | Seed phrases that are incomplete, jumbled, or have a few incorrect words. | A nearly complete list of the seed phrase words. | The number of missing or incorrect words in the phrase. |
Choosing the right approach is the first and most critical decision in any digital asset recovery attempt. By matching your specific problem to the correct specialized tool, you maximize your chances of success and avoid making a bad situation worse.
When your crypto is stolen, not just lost, the game changes. You're no longer dealing with a technical puzzle; you're dealing with a crime. While cracking a forgotten password is one thing, cracking a criminal case is another beast entirely.
The good news is, you don't have to face it alone. Agencies like the FBI and the U.S. Secret Service have gotten remarkably good at blockchain tracing. They can follow the digital breadcrumbs left by thieves, using the public nature of the blockchain as a powerful tool. Involving them isn't a long shot anymore—it's a real, albeit often slow, path to getting your assets back.
Taking the First Step: Filing a Report
The second you confirm your crypto has been stolen, your first move should be to file an official report. If you're in the U.S., the main place to do this is the FBI's Internet Crime Complaint Center (IC3). Think of this report as the official starting pistol for any investigation.
Get ready to provide as much detail as you can. They'll need things like:
- Transaction Hashes: These are the unique IDs for the transactions that moved your funds.
- Wallet Addresses: Your wallet address and, crucially, the addresses the thief sent the funds to.
- Communication Records: Any emails, weird messages, or website history related to the hack or scam.
The more evidence you hand over, the stronger their case will be from the get-go. A detailed report can make a huge difference in how quickly things get moving.
Whatever you do, preserve every single piece of evidence. Don't delete that sketchy email or clear your browser history. This digital paper trail is exactly what investigators need to build their case and trace the thieves across the blockchain.
How Law Enforcement Gets Stolen Crypto Back
It's not a fast process, but it can be incredibly effective. Once you file a report, specialized cybercrime units get to work on what's called on-chain analysis. They painstakingly trace the stolen funds as they move from wallet to wallet, even when thieves use complex "mixing" services to try and cover their tracks.
Their main goal is to follow the money until it hits a centralized exchange where the thief tries to cash out into traditional currency. That's the moment of truth.
When that happens, law enforcement can hit the exchange with legal orders like subpoenas or seizure warrants. This legally compels the exchange to freeze the funds and reveal the identity of the person who owns the account, creating a direct link to the criminal. This kind of cooperation between global agencies and exchanges is vital for fighting these borderless crimes.
And these operations are getting bigger and more successful. As regulations have become clearer since 2023, the whole recovery landscape has shifted. For instance, in mid-2025, press reports revealed that the U.S. had centralized nearly $400 million recovered by the Secret Service alone through these kinds of seizures. It's a clear sign that the system is working. You can read more about these recent updates in digital asset regulation to see how the legal environment is changing.
Making the jump from trying to recover a password yourself to launching a legal case is a big step. It demands a lot of patience and realistic expectations, as these investigations can take months or even years. But for anyone who's been a victim of theft, it’s the most powerful way to hold criminals accountable and, hopefully, reclaim what’s yours.
So you're locked out of your wallet. Now what?
You’re basically at a fork in the road. One path is the Do-It-Yourself (DIY) route, a rabbit hole of open-source tools and online forums. The other path leads to professional services, where you hand the problem over to an expert. Which way you go really depends on what's at stake, how tech-savvy you actually are, and how much risk you're willing to stomach.
The DIY path can seem appealing, especially if you're technically inclined. You get to stay in control, and you don't have to pay any service fees. But be warned: this path is littered with landmines. One wrong move or a misunderstood command can wipe your data for good, turning a recoverable situation into a complete loss.
It's a bit like trying to perform surgery on your own hard drive. Without the right tools and a deep understanding of what you're doing, the odds of causing permanent damage are incredibly high. The learning curve is steep, and a mistake could cost you everything.
Thinking About the DIY Recovery Path
Before you even think about downloading a piece of recovery software, you need to have an honest chat with yourself. Are you really equipped for this? DIY is usually only a good idea for low-value assets where a total loss would be a bummer, but not a financial catastrophe. Think of it as a space to experiment, not a place to gamble your life savings.
Here’s what to consider before you dive in:
- Your Real Technical Skill: Do you truly understand things like file systems, cryptography, and how to use a command-line interface? A little bit of knowledge can be a dangerous thing here.
- The Risk of Permanent Loss: The biggest danger is accidentally overwriting the very data you’re trying to recover. Many DIY tools are destructive if you use them incorrectly, and they can permanently erase any chance of getting your assets back.
- The Time You'll Spend: This isn't a quick fix. You could be looking at days, or even weeks, of running processes, digging through forums, and trying to troubleshoot cryptic errors.
When to Call in a Professional
There's a reason professional recovery services exist. They have specialized hardware, proprietary software, and years of hard-won experience—things the average person just doesn't have access to. This massively boosts the odds of a successful recovery, especially for complicated cases.
Think of professionals as a digital bomb disposal squad. They know exactly which wires to cut and in what order, minimizing risk with every step. Yes, their services cost money, but you're paying for expertise and a much, much higher chance of success. If the assets you're trying to recover are significant, hiring a pro isn't a luxury—it's just a smart, calculated decision.
A good sign of a reputable recovery firm is a success-based fee. This means their interests are perfectly aligned with yours. They only get paid if they get your funds back. It's one of the most important things to look for in a trustworthy service.
How to Vet a Digital Asset Recovery Company
Choosing the right company is absolutely critical. Not all recovery services are created equal, and frankly, the industry has its fair share of shady operators. You have to do your homework to protect yourself and your assets.
Here are the key questions you should ask any company you're considering:
- What’s your fee structure? You should insist on a "no win, no fee" policy. Be very suspicious of anyone asking for large, non-refundable payments upfront.
- What are your security protocols? How are they going to protect your sensitive data and wallet files? They should be able to clearly explain their data handling, encryption, and privacy policies.
- Can you show me your track record? Ask for case studies, testimonials, or reviews you can verify. A proven history of success is non-negotiable.
- What's your process? A legitimate company will walk you through their process step-by-step, including giving you a realistic timeline.
Asking these simple questions will help you tell a legitimate asset recovery company from a potential scam. Making a smart, informed choice right now is the single most important thing you can do to get your assets back safely.
How to Prevent Future Asset Loss
The best way to deal with digital asset recovery is to make sure you never need it in the first place. Seriously. Shifting your mindset from reacting to a crisis to proactively protecting your assets is the single smartest move you can make. The painful lessons from losing crypto often give us the perfect blueprint for building stronger defenses.
Think of your digital holdings like a physical treasure. You wouldn't leave gold coins sitting on your coffee table; you'd lock them in a vault. The same logic applies here, and it all starts with your passwords.
Strengthen Your Digital Locks
Your first line of defense is just good password hygiene. Using a trusted password manager is non-negotiable these days. It lets you create and store ridiculously complex, unique passwords for every single account without needing a photographic memory. This one step immediately stops a breach on one site from spiraling into a total compromise of your digital life.
But for crypto, the gold standard is how you handle your seed phrase. A slip of paper is just too fragile—easily lost, damaged, or thrown away. You need to think more durably.
- Steel Plates: Etching your seed phrase onto a fireproof and waterproof steel plate means it can literally survive a house fire or flood.
- Secure Distribution: Never, ever keep your entire seed phrase in one spot. Split it up and store the pieces in different, highly secure locations, like a safe deposit box and with a trusted family member. This adds a powerful layer of redundancy.
This decision tree gives you a clear picture of when to try recovering assets yourself versus when it's time to call in the professionals.
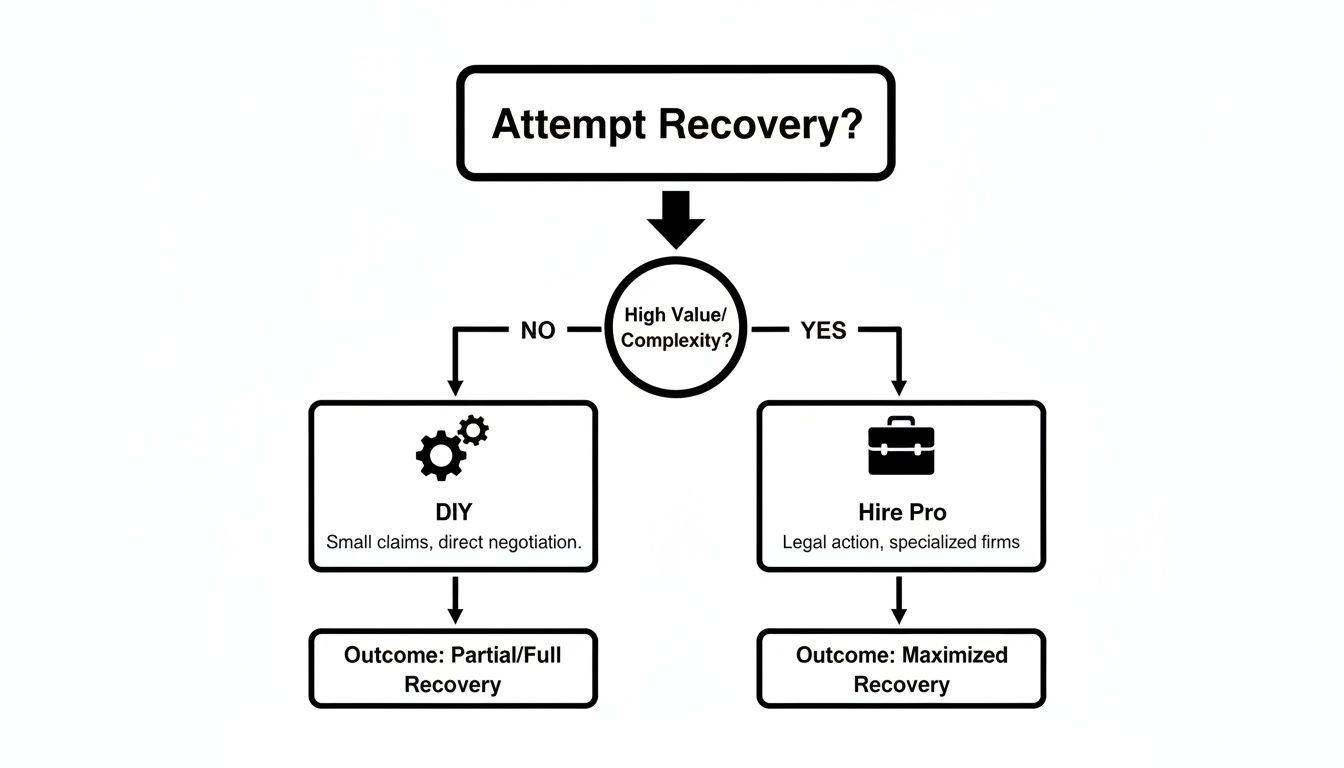
As the flowchart shows, while DIY methods have their place, professional services are the way to go for anything complex or high-value. You don't want to risk accidentally locking yourself out for good.
Isolate Assets from Online Threats
Another game-changing step is to get your assets offline entirely. Hardware wallets, like those from Ledger or Trezor, store your private keys on a physical device that stays disconnected from the internet. This makes them virtually immune to online hacks, malware, and phishing scams.
Think of a hardware wallet as your own personal, offline bank vault. Transactions are signed inside the secure device itself, which means your private keys are never exposed to your potentially compromised computer or phone.
Finally, stay paranoid about scams. Be deeply skeptical of unsolicited offers, random DMs, and "support" agents reaching out to you. Always double-check any communication through official websites or apps, and burn this rule into your brain: never share your seed phrase or private keys with anyone. For any reason. Ever.
By putting these simple security habits into practice, you build a fortress around your assets. Spending a little time securing them today is a whole lot less stressful than scrambling to recover them tomorrow. For a deeper dive, our guide provides everything you need for creating a secure Bitcoin wallet backup.
Common Questions About Digital Asset Recovery
Stepping into the world of digital asset recovery can feel like a minefield. It’s totally normal to have a lot of questions, so let's tackle some of the most common ones head-on.
How Much Does Professional Digital Asset Recovery Cost?
This is usually the first thing people ask, and for good reason. The good news is that reputable recovery services almost always work on a success-based fee. It’s simple: you don’t pay a dime unless they get your crypto back.
This fee is a percentage of the recovered funds, typically somewhere between 10% and 20%. The final number really depends on how tricky your specific case is—things like the wallet type and how many clues you can provide make a big difference.
A word of warning: be extremely wary of anyone asking for a big, non-refundable payment upfront. That’s one of the biggest red flags in this industry and often a sign of a scam. A legitimate service only wins when you win.
Can Crypto Be Recovered From a Broken Device?
Surprisingly often, yes. Getting crypto off a broken phone, dead laptop, or fried hard drive is possible through a field called digital forensics. It all comes down to the physical memory chip where your data was stored.
If that chip is still intact, forensic specialists can usually pull the raw data containing your wallet files or private keys, even if the device itself is a brick. Success rates are quite high for things like software corruption or even water damage (as long as you act fast). The odds get a lot slimmer, though, if the memory chip has been physically shattered or completely fried.
What Is the Success Rate for a Lost Seed Phrase?
Let's be crystal clear on this one: recovering a completely forgotten 12 or 24-word seed phrase from thin air is impossible right now. The cryptography behind it is just too powerful.
But the story changes completely if you have partial information. The chances of a successful recovery shoot way up if you have:
- Most of the words: Maybe you know 11 out of 12 words, or 23 out of 24.
- All the words, but in the wrong order: You’ve got the full list, you just don't know the right sequence.
In these situations, specialists can use high-powered software to brute-force every possible combination using the pieces you provide. The more correct parts of the puzzle you have, the better your chances are of putting it all back together.
If you're staring at a locked wallet and need an expert eye, the team at Wallet Recovery AI uses advanced, secure methods to help you get back in. Our entire process is confidential and built to give you the best possible shot at success. Find out more about how we can help at https://walletrecovery.ai.


Leave a Reply