That gut-wrenching moment you log in and see a zero balance where your crypto should be is something I wouldn't wish on anyone. It feels like the floor has dropped out from under you. Panic is the first thing that hits, but letting it take over is the worst thing you can do.
What you do in the next 60 minutes is more critical than anything that comes after. This isn't just about damage control; it's about preserving the digital breadcrumbs that could lead you back to your funds.
What to Do When Your Crypto Vanishes

The first rule is to stop the bleeding. Assume everything is compromised. Every device, every account, every password.
Your absolute top priority is to move any remaining funds out of the affected wallet immediately. Transfer them to a brand-new, secure wallet—one you create on a completely separate, clean device. Don't just create a new wallet on the same potentially infected computer; that's like bailing water out of a sinking boat with a hole in the bucket.
Isolate and Secure Your Digital Environment
Once your remaining assets are safe, it's time to quarantine the breach. Pull the plug. Disconnect the affected computer or phone from the internet.
This stops the attacker in their tracks. They can't dig deeper into your system, steal more data, or try to cover their tracks by deleting the malware they used. Think of it like a house fire. You don't start sifting through the ashes to find the cause while the flames are still spreading. You contain it first.
Document Everything Meticulously
Now, put on your detective hat. Under this kind of stress, your memory is unreliable. You need to write down every single detail you can think of, no matter how small it seems. This documentation is the lifeblood for law enforcement and any recovery specialists you bring in.
Create a timeline. Get specific.
- The moment of discovery: When did you first notice the funds were gone? What were you doing just before?
- Suspicious activity: Did you click a weird link? Download a new app? Approve a transaction you didn't recognize? Jot down the exact websites, emails, or messages.
- Scammer communications: If you were tricked, screenshot every conversation on Telegram, Discord, email, or wherever it happened. Do not delete anything.
- Wallet addresses: Write down your compromised wallet address and the address(es) the thief sent your funds to.
Key Takeaway: The quality of your notes directly impacts your chances of recovery. A vague story is a dead end. A detailed log gives investigators a trail to follow.
I've seen cases where a victim took screenshots of the fake phishing site and noted the exact time they entered their seed phrase. That single piece of information gave investigators the hook they needed to start unraveling the attacker's entire setup.
Locate the Transaction Hash
Last, but definitely not least, you need to find the transaction hash (also called a TXID). This is the long string of letters and numbers that acts as the unique receipt for the theft on the blockchain. It's the most important piece of evidence you have.
You'll find it in your wallet's transaction history. Once you have it, you can plug it into a block explorer like Etherscan (for Ethereum) or Blockchain.com (for Bitcoin) to see exactly where your crypto went. This TXID is the first thread that recovery experts will pull to trace the stolen assets.
To help you stay focused during a high-stress situation, here's a quick checklist of the immediate steps we just covered.
Immediate Action Checklist for Crypto Theft
| Action Item | Why It's Critical | Example |
|---|---|---|
| Move Remaining Funds | Stops further losses from the compromised wallet. | Transfer any remaining ETH or tokens to a new MetaMask wallet created on a separate, trusted computer. |
| Disconnect from Internet | Prevents the attacker from stealing more data or covering their tracks. | Unplug the Ethernet cable from your desktop or turn off Wi-Fi on your laptop and phone. |
| Document All Details | Creates an evidence log for law enforcement and recovery services. | Take screenshots of the scammer's Discord messages, note the URL of the phishing site you visited. |
| Find the Transaction Hash | Provides the primary breadcrumb for tracing the stolen funds on the blockchain. | Copy the TXID from your wallet's transaction history and paste it into Etherscan to view the transfer. |
Acting quickly and methodically on these first few steps can make all the difference. It shifts you from being a victim to being an active participant in your own recovery.
Following the Digital Breadcrumbs of Your Stolen Crypto

Once you've contained the immediate damage, it's time to go on the offensive. The blockchain’s greatest strength—and in this case, its greatest weakness for thieves—is its total transparency. Every single transaction is carved into a public ledger forever. That digital trail is your roadmap, and learning to read it is your first real step toward recovery.
The most critical piece of evidence you have right now is the Transaction ID (TXID), sometimes called a transaction hash. This unique string of characters is your starting point. You can copy this ID and paste it directly into a public block explorer for whatever crypto was stolen.
- For Ethereum (ETH) and any ERC-20 tokens: Use an explorer like Etherscan.
- For Bitcoin (BTC): Head over to an explorer like Blockchain.com or Blockstream.
- For other chains (Solana, BSC, etc.): Each blockchain has its own dedicated explorer, like Solscan for Solana or BscScan for Binance Smart Chain.
When you pop the TXID into the right explorer, you’ll immediately see the thief's wallet address—the first destination for your funds. This is link number one in a chain you're about to follow.
How to Follow the Money on the Blockchain
From that initial wallet, you can click on its address to see every transaction it has ever made, both in and out. Think of yourself as a digital detective. The goal is to trace the money from one wallet to the next, mapping out every hop it takes.
Honestly, this part can feel like you're trying to untangle a massive, knotted ball of yarn. Thieves almost never move stolen funds straight to an exchange to cash out. Why would they? Their entire goal is to break the chain of evidence and launder the funds, making your life harder.
For example, a scammer might send your stolen ETH to a fresh wallet, immediately swap it for a privacy coin like Monero using a decentralized exchange, and then send it to yet another address. They’re building a maze on purpose to throw you off the trail.
The Thief's Toolkit: Mixers and Tumblers
One of the most common tricks in the book is using a mixer or tumbler. These services are specifically designed to muddy the waters and sever the on-chain link between a user's old and new addresses.
Imagine a giant digital pot where thousands of people throw in their crypto. The service "mixes" it all up and then spits out the equivalent amounts to new, clean wallets. This makes it incredibly difficult to prove that the funds that came out are the exact same funds that went in.
A Note from the Trenches: While mixers are a major headache, they aren't a dead end. Advanced forensic tools can often "de-mix" these transactions. By analyzing transaction timing, volumes, fees, and other metadata, it's often possible to identify the most likely path your funds took through the service.
This kind of analysis is deep, technical work. This is where firms that specialize in blockchain forensics really shine, using powerful software to piece together transaction patterns that are invisible to the naked eye.
Spotting the Off-Ramps: Where Crypto Becomes Cash
At the end of the day, most thieves want to turn their stolen crypto into cold, hard cash (like USD or EUR). To do that, they have to use an "off-ramp," which is almost always a centralized cryptocurrency exchange.
These exchanges are the bottlenecks. To stay in business, they have to follow strict Know Your Customer (KYC) and Anti-Money Laundering (AML) laws. This means they force users to verify their real-world identity with a driver's license, passport, and other personal documents.
When you and your legal team successfully trace the stolen funds to a deposit address at a major exchange like Coinbase, Binance, or Kraken, you've hit a critical milestone. This is the point where law enforcement can get involved with subpoenas and court orders. They can compel the exchange to freeze the funds and, most importantly, reveal the identity of the account holder. Finding that off-ramp is often the key to getting your crypto back.
Once you’ve traced the stolen crypto as far as you can on your own, it's time to call in the professionals. A lot of people skip this step, figuring that crypto is the "wild west" and the police can't do anything. That's a huge mistake. If you're serious about getting your funds back, involving law enforcement is non-negotiable.
Filing a police report creates the official paper trail you absolutely need for any future legal action. But you can't just walk in and say, "my crypto was stolen." You'll be met with blank stares. You have to walk them through it, connecting the digital dots to a real-world crime they can understand.
How to File a Police Report That Actually Gets Attention
To get law enforcement to take your case seriously, you need to hand them a file with specific, actionable intelligence. They aren't blockchain experts, so your job is to do the heavy lifting for them.
Here’s what you absolutely must have ready:
- A Detailed Timeline: Write down the exact sequence of events, from the moment you noticed something was wrong. Include dates and times.
- Transaction Hashes (TXIDs): This is your smoking gun. Provide the main transaction ID showing the funds leaving your wallet.
- Wallet Addresses: List your compromised address and every address the thief sent the funds to.
- Scammer Communications: Get screenshots of everything—every chat, email, or message you exchanged with the attacker.
- The Financial Damage: State the exact amount of crypto stolen and what it was worth in fiat (like USD or EUR) at that moment.
Think of it this way: you're not just reporting a crime, you're handing investigators their starting point on a silver platter. The better organized your information, the better your chances of getting your case moved to the top of the pile. This isn't just a theory; the data backs it up.
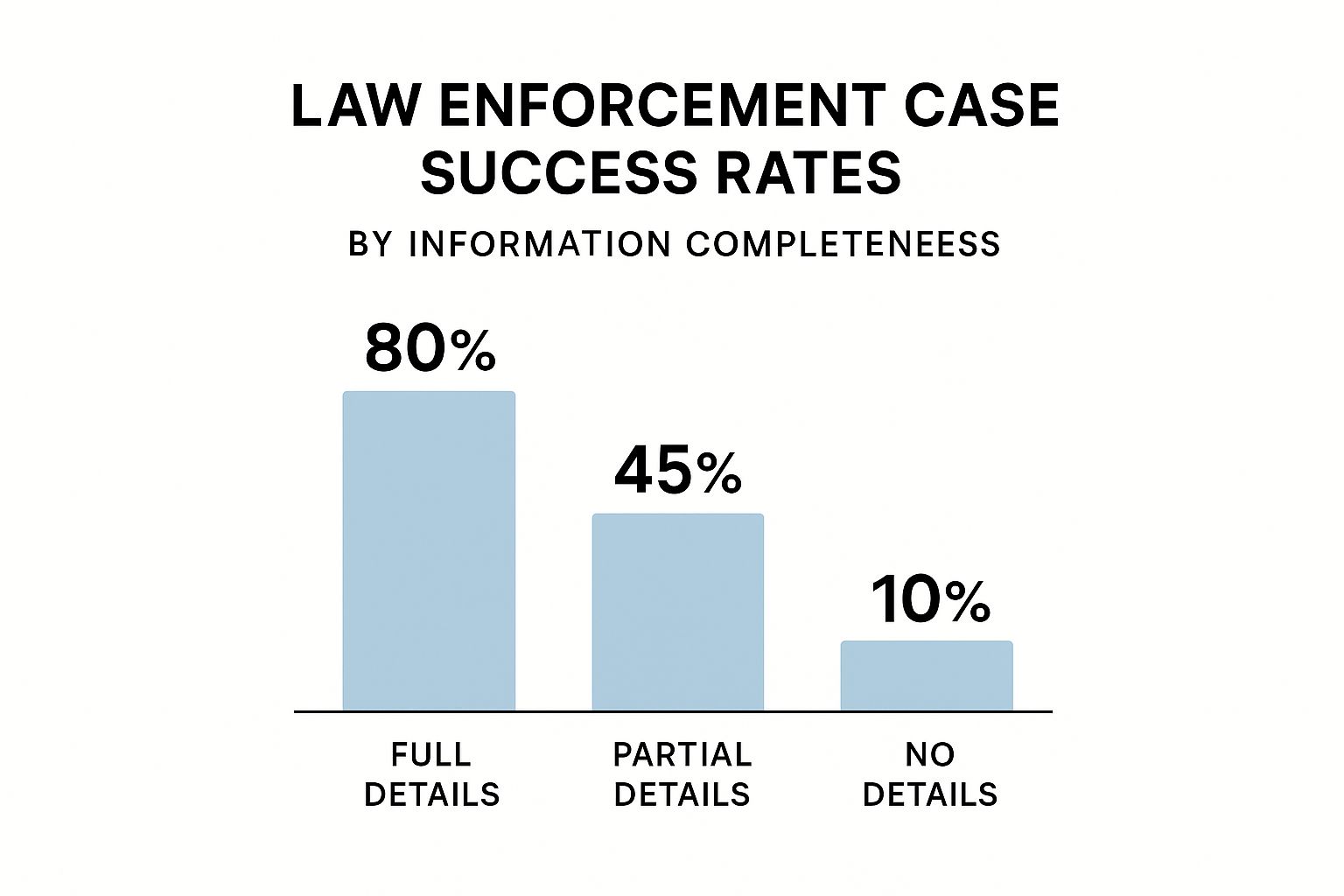
As you can see, a complete, well-documented report can dramatically swing the odds in your favor. It turns a long shot into a real possibility.
Taking Your Case to Federal Agencies
If you've suffered a significant loss, your local police station is just the first stop. You also need to report the theft to federal agencies that handle cybercrime. In the U.S., that means filing a complaint with the FBI’s Internet Crime Complaint Center (IC3).
When you file with the IC3, your case enters a national database. This allows agents across the country to spot patterns and connect your theft to larger criminal rings, especially if the crime crosses state or international borders. This is a critical move if your funds were traced to an exchange that operates under U.S. jurisdiction.
Expert Insight: Law enforcement agencies tend to prioritize cases based on two things: the amount stolen and the quality of the evidence. A well-documented report filed with both local police and the IC3 makes your case much harder to ignore.
Knowing When to Bring in a Crypto Law Expert
While the police can investigate, they can't act as your personal lawyer. To actually freeze accounts and recover your assets, you'll almost certainly need to hire an attorney who specializes in cryptocurrency and asset recovery.
These legal pros are worth their weight in gold for a few key reasons:
- They Know the Ropes: They understand how to draft and file subpoenas, court orders, and other legal documents needed to compel exchanges to cooperate.
- They Force Compliance: An exchange will almost always ignore an email from a victim. They can't ignore a formal legal demand from a law firm.
- They Can Freeze Assets: A lawyer can file an injunction to freeze the thief's account at an exchange before the funds are cashed out and gone for good.
Recovery rates vary, but legal muscle is a game-changer. Successful recoveries often bring back between 40% and 70% of the stolen crypto, even after legal fees. Where the crime happens matters, too. North America and the EU see higher recovery rates of 45-55% thanks to stronger legal systems, compared to Asia's 30-40%. You can learn more about the state of crypto recovery statistics and success rates to see how these global differences play out. It just goes to show how vital a good legal team is for tackling these complex, cross-border cases.
Losing your crypto is a gut-wrenching experience. That mix of panic and desperation can make you vulnerable, and unfortunately, that’s exactly what a whole new breed of scammers is counting on. They’re called recovery room scammers, and they prey on victims, promising the world just to take what little you have left.
Navigating this space is tricky, but learning to spot the predators from the real partners is the most critical next step you can take.
The absolute biggest red flag? Anyone who guarantees they can get your money back. Let me be crystal clear: no one can promise a 100% recovery. The process is a minefield of complexities, from funds being laundered through mixers like Tornado Cash to dealing with uncooperative offshore exchanges. A legitimate expert will give you an honest, sober assessment of your chances, not sell you a fantasy.
Another dead giveaway is a demand for a large upfront fee. Scammers love this. They’ll disguise it as a "processing fee," a "network tax," or some other official-sounding nonsense. If you're asked to pay a hefty sum before a single satoshi is recovered, run. Don't walk, run.
What a Real Recovery Partner Looks Like
So, what separates the pros from the predators? Real crypto recovery specialists operate with the transparency and professionalism you’d expect from a high-end financial or legal firm. They know their way around blockchain forensics, international law, and the delicate dance of law enforcement cooperation.
Their entire business model is built on success, not on squeezing victims.
The gold standard for payment is a contingency-based fee. This is simple: they only get paid if you get paid. They take a percentage of the recovered assets, usually somewhere between 10% to 30%. This structure puts you on the same team. Their success is tied directly to yours, meaning they won't take your case unless they genuinely believe they can win.
My Two Cents: A contingency fee is everything. It shows the firm has skin in the game. They’re investing their own time, money, and resources because they're confident in their skills and the merits of your case.
On top of that, a credible firm will have a track record you can actually verify. They should be able to point to case studies (with sensitive details blacked out, of course), real client testimonials, or professional references. Their team should be a mix of cybersecurity pros, blockchain analysts, and legal experts. Anything less is a major red flag.
Questions You Absolutely Must Ask
Before you even think about signing anything, you need to put any potential service through its paces. Think of it as a job interview, and you're the one doing the hiring.
Get on a call and hit them with these questions:
- How do you get paid? Demand a crystal-clear, written explanation of their fee structure. If it’s not primarily based on contingency, you should be extremely skeptical.
- What's your game plan? They need to walk you through their process. This should involve on-chain tracing, coordinating with exchanges, and leveraging legal avenues. If their explanation is vague or full of confusing jargon, they’re hiding something.
- Show me you've done this before. Ask for anonymized case studies or examples of situations similar to yours.
- Who’s on my team? A real operation has a blend of technical and legal talent. A group of self-proclaimed "blockchain wizards" without any legal counsel is a recipe for disaster.
- How will we stay in touch? You deserve regular, straightforward updates. Don't settle for anything less.
It boils down to this: a real service acts like a law firm, offering counsel and a clear strategy. A scam operates like a high-pressure sales pitch, armed with vague promises and urgent demands for cash.
To help you tell them apart at a glance, here’s a quick comparison.
Legitimate vs Scam Recovery Services
Spotting the difference between a genuine recovery expert and a scammer is crucial. This table breaks down the key characteristics to watch for, helping you avoid falling victim a second time.
| Characteristic | Legitimate Service | Scam Operation |
|---|---|---|
| Payment Model | Primarily contingency-based (a % of recovered funds). | Demands large upfront fees before any work is done. |
| Guarantees | Provides a realistic assessment of success; never guarantees it. | Promises 100% guaranteed recovery to lure you in. |
| Transparency | Clearly explains their process, team, and legal strategy. | Vague about methods; uses confusing technical jargon. |
| Communication | Professional, responsive, and provides regular case updates. | High-pressure tactics, creates false urgency, and goes silent after payment. |
| Track Record | Has a verifiable history of success and professional online presence. | Lacks a real history; may use fake testimonials and stock photos. |
Choosing the right partner is arguably the most important decision you'll make in this entire ordeal. A little due diligence now can be the difference between getting your assets back and getting burned all over again.
Strengthening Your Defenses to Prevent Future Thefts

Getting your crypto back after a theft is a brutal fight. The real win, though, is making sure you never land in that position again. A successful recovery is meaningless if your security posture stays the same. It's time to turn a painful experience into a masterclass in digital self-defense, building a true fortress around your assets.
The first, absolute must-do is upgrading to a hardware wallet. If you're holding any serious amount of crypto, a device from a company like Ledger or Trezor isn't just a good idea—it's essential. A hardware wallet keeps your private keys entirely offline, making them invulnerable to the malware and phishing schemes that constantly plague online software wallets.
Think of it this way: your MetaMask wallet is like a billfold in your back pocket. It's convenient, but it's also exposed. A hardware wallet is your own personal bank vault. Even if a thief knows where it is, they can't get inside without the physical device and its PIN. It's a small investment for what is arguably the single biggest security upgrade you can make.
Adopting Advanced Wallet Security
For those with larger portfolios, even a single hardware wallet might not cut it. The next level of protection is a multi-signature (multisig) wallet. This kind of setup requires authorizations from multiple private keys before any transaction can be approved.
It’s like a bank safe deposit box that needs two separate keys, held by two different people, to open. A common 2-of-3 multisig setup creates three private keys, but requires any two of them to sign off on sending funds. This immediately makes an attacker's job exponentially harder—they’d have to compromise two of your secure devices, not just one.
Pro Tip: When you set up a multisig wallet, store each key in a different, secure geographic location. Never, ever keep them all in the same house. This protects you from a physical theft, but also from disasters like a fire or flood.
This kind of layered defense is non-negotiable for anyone serious about holding crypto for the long haul. You can dive deeper into these strategies by exploring our other articles on advanced crypto security.
Defending Against Sophisticated Attack Vectors
The truth is, hackers are always leveling up. They're moving beyond basic phishing emails to far more complex and personal attacks, and knowing what you're up against is half the battle.
One of the most terrifying is the SIM-swapping attack. This is where a scammer tricks your cell phone provider into transferring your phone number over to a SIM card they control. Once they have your number, they start intercepting all your two-factor authentication (2FA) codes sent via SMS. Just like that, they can get into your email, your exchange accounts, and anything else tied to that number.
Here's how you shut that down:
- Use Authenticator Apps: Ditch SMS-based 2FA immediately. Switch to app-based authenticators like Google Authenticator or Authy. These apps generate codes locally on your device, so they can't be intercepted by a SIM swap.
- Set a Port-Out PIN: Call your mobile provider and ask to set up a unique PIN or password for your account. This adds a crucial layer of security, as the carrier will require this code before porting your number to a new device.
And it's not just lone-wolf hackers you're up against. The threat landscape now includes state-sponsored groups. For instance, North Korea-linked hackers stole over $2 billion in crypto in 2025 alone, funneling the money directly into their military programs. This isn't amateur hour; individual investors are now facing threats from highly organized, well-funded global enterprises. Building a robust defense has never been more critical.
Common Questions About Crypto Recovery
When your crypto gets stolen, your head is probably spinning with a million questions. It’s a gut-wrenching experience, and the path to getting your assets back feels anything but clear. Let's cut through the confusion and tackle some of the most common questions I hear from victims.
Getting straight answers is the first step toward setting realistic expectations and making smart decisions when the pressure is on.
Is It Actually Possible to Recover Stolen Cryptocurrency?
The short answer is yes, it's possible. But it's never, ever a guarantee.
Success really boils down to a few critical factors: how fast you act, how sophisticated the thief was, and whether exchanges and law enforcement will cooperate. Unlike a simple bank transfer you can reverse, blockchain transactions are final. There's no "undo" button.
The real goal isn't to reverse the transaction. It's to trace the stolen funds across the public ledger until they hit an "off-ramp"—usually a centralized exchange where the thief has to reveal their identity to cash out. Once the funds are there, legal action can force the exchange to freeze the assets and unmask the person behind the account.
How Much Does Hiring a Crypto Recovery Service Cost?
This is a big one, and the answer separates the legitimate services from the scammers.
Legit recovery firms almost always work on a contingency fee model. They take a percentage of what they successfully get back for you, which typically ranges from 10% to 30%.
If a service demands a huge, non-refundable payment upfront, run. That's the biggest red flag out there. Some reputable firms might ask for a small retainer to cover the initial deep-dive forensic analysis, but their main paycheck should always be tied to getting your money back.
Key Insight: A contingency fee means their goals are perfectly aligned with yours. They don't get paid unless you do, which is exactly how it should be.
How Long Does the Crypto Recovery Process Take?
There’s no one-size-fits-all timeline. A recovery effort can take a few weeks or drag on for more than a year. Every single case is different.
- Faster Cases: If the thief made a simple mistake—like moving the funds directly to a major, cooperative exchange in a well-regulated country—things can move relatively quickly.
- Longer Cases: On the other hand, if you're dealing with a pro who used mixers, chain-hopped across different blockchains, or sent the funds to an exchange in a shady jurisdiction, you're in for a long haul. It becomes a drawn-out legal and investigative battle.
Patience is an absolute must. The painstaking forensic work, the back-and-forth with law enforcement, and the legal hurdles all take time.
Can I Recover Stolen Crypto by Myself?
You should absolutely take the first few steps on your own. Securing your remaining accounts, gathering all the evidence you can, and using a block explorer to start tracing the funds are things you can and should do immediately.
But a full-scale recovery effort? That's a different beast. Going it alone is incredibly difficult, and this is where pros bring a few things to the table that most people just don't have:
- Advanced Forensic Tools: They have access to specialized software that can de-anonymize complex transaction trails that look like a dead end to the naked eye.
- Established Networks: They already have relationships with compliance departments at major exchanges and contacts within law enforcement agencies. This can cut through a ton of red tape.
- Legal Know-How: They know exactly how to file the correct subpoenas and court orders to get assets frozen—a process that is bewildering for the average person.
While it's not technically impossible to do it yourself, partnering with specialists dramatically increases your odds of actually seeing your crypto again.
If you've lost access to your funds or had them stolen, the journey to recovery can be daunting. The team at Wallet Recovery AI combines advanced technology with expert guidance to help you reclaim your digital assets safely and discreetly. Learn how we can help you regain control of your wallet.
Article created using Outrank


Leave a Reply