That gut-punch feeling when a password fails is something we've all felt. Panic is the first instinct, but it's the last thing you should do. A calm, methodical approach is your best friend right now. Before you even think about complex recovery, let's rule out the simple human errors that cause a surprising number of lockouts.
Start with the absolute basics. Seriously. Is Caps Lock on? Did you accidentally add a space at the end? It sounds almost silly to mention, but these little slip-ups are incredibly common. Also, take a half-second to make sure you're on the right website and not a clever phishing look-alike.
For a normal online account—think email or social media—the "Forgot Password" link is your next stop. It’s a straightforward process: it sends a reset link to your email or a code to your phone. If you don't see it in your inbox, always check your spam folder. Those automated emails get flagged all the time.
The High-Stakes World of Crypto Wallets
Now, if you're staring down a locked crypto wallet, the game changes entirely. There's no customer service desk, no central authority, and no simple "Forgot Password" link to save you. A forgotten password here can mean your assets are gone forever.
It's not an exaggeration. A staggering 20% of all Bitcoin in existence is believed to be permanently lost, much of it locked away behind forgotten passwords. That statistic alone should tell you why a meticulous, step-by-step diagnostic is crucial before you do anything else.
So, when it's a crypto wallet, your initial checklist needs to be more thorough.
Before you go any further, it's wise to create a quick action plan. I've put together a table that outlines the first things you should check, moving from the simplest fixes to the slightly more involved initial steps.
Initial Recovery Action Plan
| Action | Why It's Important | Best For |
|---|---|---|
| Check for Typos & Caps Lock | Rules out the most common human errors immediately, preventing unnecessary stress. | All password-protected accounts. |
| Verify the Wallet File/Software | Ensures you're not trying to access the wrong backup or using incompatible software. | Crypto wallet files (wallet.dat, keystore JSON). |
| Brainstorm & Document Password Hints | Captures fragments of memory before they fade. Every partial hint is a valuable clue. | Crypto wallets and any password you created yourself. |
| Use a "Forgot Password" Link | The standard, automated recovery method for centralized services. | Email, social media, online banking, exchanges. |
| Check Password Manager Vaults | If you use one, you might have saved an old version or the correct password there. | Anyone who uses a password manager. |
This checklist is your starting line. Working through it systematically ensures you've covered all the low-hanging fruit before deciding you need to dig deeper.
This decision tree gives you a visual path for these first few moments of panic.
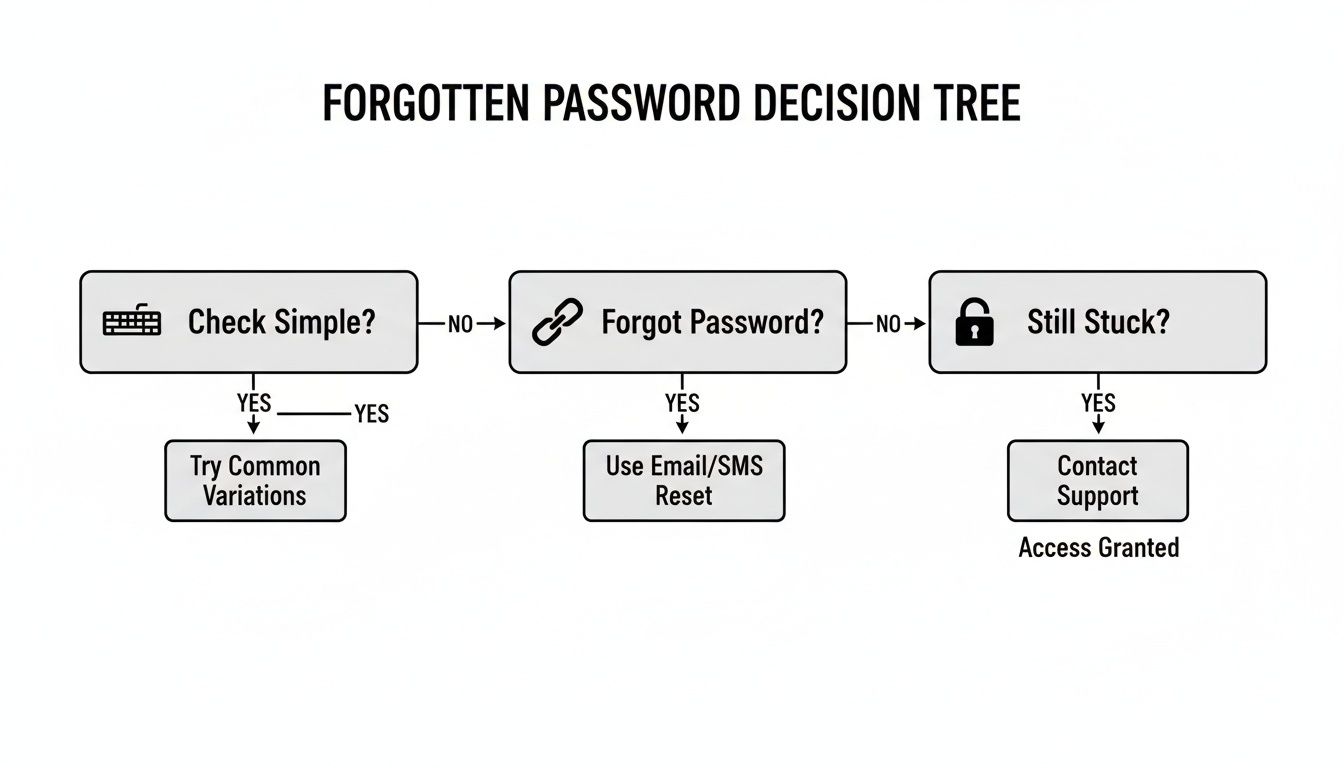
The whole point is to exhaust the simple fixes before you conclude you need more advanced help. By taking these preliminary steps, you build a solid foundation for any deeper recovery efforts that might be necessary. For more ideas on jogging your memory, you can explore our full guide on how to find forgotten passwords.
Safe DIY Crypto Wallet Recovery Techniques
Before you even think about calling in the professionals, the safest and most private way to get your assets back is to try recovering them yourself. You’re in complete control, and nobody knows your digital habits better than you do. The whole idea is to be methodical, stay safe, and avoid the common mistakes that can make things worse.
This is your show. You know the weird quirks, the old inside jokes, the pet names you might have used. The goal here is to tap into that personal knowledge and use the tools you already have without putting your funds at risk.

Unlocking Your Memory with a Personal Dictionary
Just randomly mashing keys and hoping for the best is a fast track to frustration. A much smarter move is to build a personal password dictionary. This isn't some high-tech hacking tool—it's just a structured list of all the bits and pieces you might have used to create that password.
Start by jotting down the core ingredients of your typical passwords:
- Base Words: Think about pet names, family members, street signs you grew up with, or your favorite movie characters.
- Significant Numbers: Old phone numbers, birthdays, anniversaries, high school graduation year—anything meaningful.
- Common Patterns: Do you always capitalize the first letter? Do you swap an 'e' for a '3' or an 'a' for an '@'? Maybe you always tack a '!' or '$' on the end.
With this list, you can start testing combinations systematically. Let's say "Fluffy" and "2015" are on your list. Now you can try Fluffy2015!, fluffy2015#, or even F1uffy2015!. It's a world away from just guessing and feels a lot less chaotic.
Handling Your Seed Phrase and Keystore Files
When it comes to crypto wallets, your seed phrase (or recovery phrase) is the skeleton key. If you have it, you can almost always get back in, no matter what the password was. The golden rule here is to never, ever type your seed phrase into a website or any online tool.
Here’s the safe way to use it:
- First, pull the plug. Disconnect your computer from the internet entirely.
- Install a fresh, clean copy of your wallet software onto this offline device.
- Choose the "restore from seed phrase" option and enter your words.
This keeps your master key completely isolated from online threats. Some wallets, like MyEtherWallet, might use a keystore file (a JSON file). This is basically your private key wrapped in an encrypted package, and it needs a password. Your personal dictionary is the perfect tool for cracking this open—just make sure you're doing it on an offline computer.
Key Takeaway: The single most critical DIY step for crypto is locating your seed phrase. If you find those 12 or 24 words, you've likely solved your problem. Protect them above all else.
These DIY methods can be incredibly successful. Just last year, services like Crypto Recovers helped users get back over $2.5 million in locked non-custodial wallets, with Bitcoin making up around 70% of that value. It just goes to show that even if you hit a wall, there are usually solid options for getting your funds back.
Hardware Wallet Recovery Insights
If you’re using a hardware wallet like a Ledger or Trezor, things work a little differently. That PIN you punch into the device? It only protects that specific piece of plastic. Forget the PIN and get it wrong too many times, and the device will wipe itself.
I know, that sounds terrifying. But it’s actually a brilliant security feature. Your crypto isn't on the device; it's on the blockchain. Your 24-word seed phrase is what truly controls your access.
As long as you have that seed phrase, you can just buy a new hardware wallet (or reset the one you have) and use the phrase to restore everything. The PIN is temporary; the seed phrase is forever. For a more detailed look at the process, check out our guide on how to recover forgotten passwords.
The Biggest Password Recovery Mistakes (And How to Avoid Them)
Trying to recover a lost password, especially for a crypto wallet, is a minefield. That feeling of panic can easily push you into making a snap decision you'll seriously regret later. The truth is, knowing what not to do is just as critical as knowing the right steps to take.
Let's walk through the most common and dangerous traps I've seen people fall into. The goal here is simple: keep you and your assets safe from both scammers and accidental self-sabotage.

The Siren Song of Shady Online Tools
When you're desperate, a random website promising "instant password recovery" feels like a godsend. These sites almost always ask you to do one of two things: upload your encrypted wallet file or, even worse, paste your seed phrase directly into a form. This is a massive, blaring red flag.
Handing over this info is the digital equivalent of giving a complete stranger the keys to your house, your car, and your safe deposit box. Scammers build these tools for one reason only—to drain your funds the second they get the details. Real recovery is a methodical process, not a magic trick.
Crucial Warning: Never, ever enter your seed phrase into any online form, website, or tool that isn't the official, verified wallet software. Even then, you should only do it on a device that is completely disconnected from the internet.
Falling for Phishing and Social Media Scams
Panic posting on public forums like Reddit or X (formerly Twitter) is a classic mistake. The second you announce you're locked out of your wallet, you paint a giant target on your back. Scammers live on these platforms, just waiting for someone vulnerable to appear.
They'll slide into your DMs, often posing as "official support" or just a helpful stranger. They might offer to help you "re-sync your wallet" or walk you through a "secure process" that, surprise, involves a screen-sharing session or clicking a sketchy link. Their only goal is to trick you into revealing your private keys or seed phrase.
This isn't a minor problem. Personal wallet compromises accounted for a staggering 23.35% of all crypto theft in a recent year. The data shows a sharp rise to 158,000 incidents hitting 80,000 unique victims, a stark reminder of the risks of fumbling a recovery attempt. If you want to see what legitimate help looks like, you can check out this breakdown of the top Bitcoin wallet recovery services in 2025.
Botching a Brute-Force Attempt
For the more technically inclined, trying to brute-force your own wallet file seems like a solid plan. The idea is to use software to hammer the file with thousands or millions of password guesses. While it can work, doing it wrong can be catastrophic.
Here's where a DIY brute-force attack usually goes south:
- File Corruption: Using poorly configured software or stopping the process incorrectly can corrupt your
wallet.dator keystore file beyond repair. Once it's unreadable, it's game over. - Wasted Time and Resources: Without a beast of a computer and an intelligent wordlist (like one built from your personal password habits), you could have a program running for months and get absolutely nowhere.
- Security Nightmares: Downloading unvetted brute-force tools from shady forums is one of the fastest ways to infect your computer with malware designed to steal everything it can find.
Unless you have a deep background in cybersecurity, a DIY brute-force attempt usually creates more problems than it solves. It’s a powerful tool, but in inexperienced hands, it's also a dangerous one. Making any of these mistakes can make it much harder—or even impossible—for a professional to help you down the line.
How to Vet Professional Recovery Services
Let's be real. There comes a point when you've tried everything. The password isn't coming back, and every failed attempt just digs the hole deeper. This is especially true in the high-stakes world of crypto, where one wrong move can torch your funds for good. Knowing when to tap out of the DIY game is a skill in itself.
So, when is it time to call in the pros? If you're staring at a corrupted wallet file, can only remember bits and pieces of a password, or you're fighting a hardware wallet that’s doing more than just asking for a PIN, it’s time. Pushing forward with random guesses or amateur scripts at this stage can actually make things worse.
Finding a Trustworthy Partner
The crypto space, for all its innovation, is also a magnet for opportunists. That means vetting a recovery service isn't just a good idea—it's absolutely critical to protecting your assets. A legitimate outfit operates with total transparency, ironclad security, and a process you can actually understand.
Start with their digital footprint. A real-deal service will have a professional website that clearly explains how they work, which wallets they support, and how to get in touch. Hunt for genuine testimonials, detailed case studies, and any mentions in reputable crypto news outlets. This is your first sniff test for credibility.
Take a look at the Wallet Recovery AI homepage, for example. It's clean, direct, and immediately tells you what they do and how they protect you.
Notice the emphasis on a straightforward, secure process. Those are the hallmarks of a service that respects you and your assets.
Critical Questions to Ask Any Service
Before you even think about sending a single file, you need to put any potential recovery partner on the hot seat. Think of it as the most important job interview you'll ever conduct, because your money is on the line. Their answers will tell you everything.
Here are the non-negotiable questions you have to ask:
- What is your exact security protocol? They need to walk you through, step-by-step, how they handle your encrypted wallet file and password hints. If they ever ask for remote access to your computer, it's a massive red flag. Hang up.
- Will you ever ask for my seed phrase? The answer must be an instant, emphatic NO. A legitimate service works with your encrypted data and password clues. They never, ever need the master key to your entire crypto life.
- What’s your fee structure? Reputable services almost always work on a success-based model. You pay a percentage of the recovered funds only after the job is done. Anyone asking for hefty upfront fees is a major warning sign.
- Can you speak to your success rate? While they might not share exact numbers for privacy, they should be able to discuss their experience confidently and provide anonymized examples or verifiable testimonials.
- How will we communicate during the process? You're looking for a team that provides regular, secure updates. Vague answers or radio silence are classic signs of a disorganized—or worse, fraudulent—operation.
Expert Insight: The seed phrase question is the ultimate litmus test. A professional's entire business model is built around not needing it. If a service so much as mentions wanting your seed phrase, run. End the conversation, block them, and never look back.
Understanding the Recovery Process
Once you've picked a service you trust, the actual process should feel secure and professional. It usually starts with a confidential consultation where you lay out the situation—what kind of wallet it is, the value at stake, and every password hint you can dredge up.
From there, they’ll give you an honest assessment of the recovery chances and a plan of attack. If you decide to move forward, you will only transfer the encrypted wallet file, never your seed phrase. The service then unleashes powerful, specialized hardware and custom algorithms to systematically test password variations based on the clues you provided.
This isn't an overnight fix. Depending on how complex your password was, the brute-force process could take a few hours or even several weeks of non-stop computation. A good partner will keep you in the loop the entire time, explaining the steps and setting realistic expectations. When you find the right team, a moment of sheer panic transforms into a structured, professional, and hopeful mission.
What Happens When You Call in the Experts?
So, you've tried everything. You've checked every note, rummaged through every password manager, and run through every possible combination you can think of. Hitting that wall is frustrating, but it’s often not the end of the road. Bringing in a specialized service can feel like a leap of faith, so let's pull back the curtain on what actually happens.
A professional service like Wallet Recovery AI doesn't work with smoke and mirrors. The process is a powerful combination of bleeding-edge computational power, smart AI, and a deep, practical understanding of how different crypto wallets are built.
The magic ingredient is actually you. Remember that list of password hints you put together? The fragments of old passwords, important dates, pet names, and personal quirks? That’s the fuel for the entire operation. Instead of you spending days manually trying a few hundred variations, these systems can test millions or even billions of possibilities per second, all guided by the clues you provide.
How AI Cracks the Code
At its core, this is a souped-up brute-force attack, but it’s a world away from blind guessing. The AI takes the breadcrumbs you provide—things like "it was around 12 characters" or "I know it had 'Dragon' and '1998' in it"—and builds a smart probability model. This model doesn't just guess randomly; it starts with the most likely combinations first, which massively slashes the time it takes to find the right one.
It’s built to test variations that would drive a person insane:
- Complex Permutations: It’ll try every possible arrangement of your clues (e.g.,
Dragon1998!,1998!Dragon,Drag@n!1998). - Character Swaps: It methodically cycles through common substitutions like swapping 'e' for '3', 'a' for '@', or 'S' for '$'.
- Keyboard Patterns: The AI also checks for common keyboard "walks" like 'qwerty' or 'asdfg' that people often tack onto their passwords.
This systematic, AI-driven approach turns a needle-in-a-haystack problem into a solvable, structured mission. It’s what makes recovery possible for passwords that would otherwise be gone for good.
Comparing Recovery Methods
Choosing a recovery path depends on your situation. A forgotten password for a test wallet is very different from being locked out of your life savings. Here's a quick breakdown of the common approaches to help you decide.
| Recovery Method | Success Probability | Security Risk | Best For |
|---|---|---|---|
| Manual Guessing | Very Low | Low | Simple, recently changed passwords you might still recall. |
| DIY Brute-Force | Low to Medium | High (if done incorrectly) | Tech-savvy users with strong password hints and powerful hardware. |
| Phishing/Scams | Zero | Extreme | Scammers and thieves. Avoid at all costs. |
| Pro Recovery Service | Medium to High | Low (with a reputable service) | Complex passwords where DIY has failed and funds are significant. |
Ultimately, professional services exist because they can safely and efficiently do what most individuals can't. They combine specialized hardware with intelligent software to maximize your odds without compromising your security.
Expertise Across All Kinds of Wallets
Not all wallets are created equal. The technique for cracking open a Bitcoin wallet.dat file is completely different from what’s needed for an Ethereum keystore or a multi-coin wallet like Exodus. This is where a professional service's deep bench of knowledge really shines.
Their expertise has to cover the whole ecosystem, from the most popular wallets to the more obscure ones:
- Software Wallets: MetaMask, Trust Wallet, Electrum, Exodus, Atomic Wallet.
- Web & Exchange Wallets: Blockchain.com, MyEtherWallet/MyCrypto.
- Hardware Wallets: Ledger, Trezor, and cases where file backups or passphrases are the only way in.
This broad support is non-negotiable. Every wallet has its own encryption quirks and file structures. A service that gets these nuances can bring the right tools to the fight, which dramatically boosts the chances of getting your funds back.
A Note on Our Process: We designed our entire system with your security as the top priority. You will never be asked for your seed phrase. The whole recovery attempt happens on your encrypted wallet file using only the password hints you give us. Your assets stay yours.
The Client Experience, Step by Step
We know how stressful this situation is, so engaging with a service like Wallet Recovery AI is built to be simple, transparent, and confidential.
Here’s what the journey looks like from start to finish:
- Secure Submission: It all starts with a confidential online form. You'll outline your situation—what kind of wallet it is, the estimated value, and every password hint you can possibly remember. More detail is always better.
- Initial Assessment: Our team reviews your case to figure out the odds of success. We’ll give you a clear picture of the potential timeline and explain our success-based fee. Simply put: you only pay if we get your crypto back.
- Encrypted File Transfer: If you give us the green light, we'll walk you through how to securely send us only the encrypted wallet file. To say it again: we never, ever ask for your seed phrase.
- The Recovery Attempt: This is where our heavy-duty hardware takes over, running our custom AI algorithms against your file. Depending on how tough your password is, this can take anywhere from a few hours to several weeks.
- Success and Handover: The moment we find the password, you'll hear from us. We’ll provide you with the correct password and guide you on how to safely open your wallet and move your funds to a new, secure address.
This entire workflow is designed to get you from that moment of panic to a final resolution, all while working with a professional team focused on one thing: securely reuniting you with your assets.
Common Questions We Hear About Password Recovery
Losing a password is stressful enough, but when crypto is on the line, the anxiety can be overwhelming. It's a journey I've seen countless people start, and most of them have the same initial questions and worries. Let's walk through some of the most common ones to give you a clearer picture of what's ahead.
How you get your password back really boils down to two things: the type of account you're locked out of and what little pieces of information you still have. Getting a handle on these details is the first real step toward getting your assets back.
Is It Actually Possible to Recover a Lost Crypto Password?
In many cases, yes, absolutely. But it's not magic. Success depends entirely on what puzzle pieces you're holding. We're not "cracking" military-grade encryption; we're using clues to intelligently reconstruct the key.
If you have your seed phrase (that list of 12 or 24 words), you're in an incredible position. Honestly, you've pretty much won. You can almost always use that phrase to restore full access to your funds on a new wallet, making the old password a non-issue.
But what if the seed phrase is gone and all you have is an encrypted wallet file, like a wallet.dat or a JSON keystore? This is where recovery becomes a high-powered guessing game. If you can provide solid hints—maybe the approximate length, words you always use, or specific number patterns—a professional service can use some serious computing power to test millions, or even billions, of combinations based on your clues.
The Hard Truth: If you have nothing—no seed phrase, no wallet file, and zero memory of how you might have structured the password—recovery is virtually impossible. Modern crypto security is just that good, and it’s designed to keep everyone out without at least one of these critical components.
How Can I Trust a Recovery Service With My Wallet?
This is the most important question you can ask. Trust is everything. A reputable, professional service builds its entire business on earning and keeping your trust. Their security isn't just a feature; it's the foundation of their entire operation.
Here’s the golden rule: a legitimate service will never ask for your seed phrase. Never. Their work is focused entirely on the encrypted wallet file and the password hints you provide.
When you’re vetting a service, look for these non-negotiable signs of a trustworthy partner:
- A Clear Privacy Policy: They must tell you exactly how your data is handled, kept safe, and ultimately destroyed after the job is done.
- Success-Based Fees: The industry standard is a "no win, no fee" model. They charge a percentage of the recovered crypto after you have it back. Anyone asking for a big payment upfront is a massive red flag.
- Verifiable Testimonials: Can you find real success stories or mentions in credible crypto publications? A good reputation is earned, not just claimed.
- A Transparent Process: They should be able to explain what they do in plain English, without hiding behind jargon. And they should never, ever ask for remote access to your computer.
What’s the Difference Between Software and Hardware Wallet Recovery?
The approach for these two is night and day, and you need to know which situation you're in.
With a software wallet (think MetaMask or Exodus), recovery usually goes one of two ways. You either use your seed phrase to restore the whole thing from scratch, or you use your password to unlock the wallet's data file on your computer.
A hardware wallet like a Ledger or Trezor is a different beast. The PIN you punch into the device itself is just to unlock that specific piece of hardware. If you forget it and guess wrong too many times, the device will wipe itself clean. That sounds terrifying, but it's not the end of the world.
Your crypto isn't on the device; it's on the blockchain. The hardware wallet is just a fancy, secure key. As long as you have that 24-word seed phrase you wrote down when you first set it up, you can buy a brand new device, enter your phrase, and get everything back. For hardware wallets, the seed phrase is everything.
If you've tried everything you can on your own and need an expert to step in, the team at Wallet Recovery AI is here to help. We use a secure, confidential, and AI-driven process to maximize your chances of success without ever needing your seed phrase. Learn more and start your recovery case today.


Leave a Reply