Hardware wallets are the gold standard for a reason. They work by keeping your cryptocurrency private keys on a dedicated, physical device, completely cut off from the internet. This offline method is called cold storage, and it's what makes your keys totally immune to online threats like viruses, spyware, and hackers.
When you need to send crypto, the transaction is signed inside the device itself. Your critical private key never, ever touches your computer or the web.
What Is a Hardware Wallet and Why Does It Matter?

Think of a hardware wallet as a tiny, personal bank vault for your digital money, where only you hold the key. Its entire job is to safeguard your private keys—the secret codes that prove you own your coins and let you spend them—by keeping them totally offline. This physical separation is the whole game, and it’s what makes these devices so incredibly secure.
This is the complete opposite of a software wallet (often called a "hot wallet"), which is just an app running on your internet-connected phone or computer. They're convenient, sure, but that constant online connection leaves them wide open to attack.
Hardware Wallets vs Software Wallets At a Glance
To really get the difference, it helps to see them side-by-side. This table breaks down the core security trade-offs between keeping your keys offline versus online.
| Feature | Hardware Wallet (Cold Storage) | Software Wallet (Hot Storage) |
|---|---|---|
| Key Storage | Private keys are stored on a secure, offline physical device. | Private keys are stored in an encrypted file on your internet-connected computer or phone. |
| Connectivity | Only connects to a computer/phone when you need to sign a transaction. | Always connected to the internet, making it accessible but vulnerable. |
| Security | Extremely high. Immune to online threats like malware, viruses, and phishing. | Lower. Susceptible to remote hacking, keyloggers, and malware infections. |
| Use Case | Ideal for storing significant amounts of crypto long-term (HODLing). | Best for small amounts of crypto used for frequent trading and daily spending. |
| Convenience | Requires physical access to the device to approve transactions, which is a bit slower. | Very convenient. Transactions can be sent quickly from anywhere with an internet connection. |
| Cost | A one-time purchase, typically between $50 and $200. | Usually free to download and use. |
Ultimately, the choice comes down to your priorities. For anyone holding a serious amount of crypto, the peace of mind offered by a hardware wallet is well worth the investment.
The Core Concept: Cold Storage vs. Hot Storage
The real difference between these wallets boils down to a single, crucial factor: their connection to the internet.
-
Hot Wallets (Software Wallets): These store your keys on a device that's online. Think mobile apps, desktop programs, or browser extensions. Their online status makes them great for quick trades, but it also means your keys are a potential target for hackers, viruses, and malware.
-
Cold Wallets (Hardware Wallets): These store your keys on a device that is never directly connected to the internet. The wallet is like a secure black box. It receives an unsigned transaction, signs it safely inside, and then passes the signed transaction back—all without your private key ever leaving the device.
A hardware wallet creates an "air gap" between your private keys and the online world. Even if your computer is riddled with malware, the keys remain untouched and secure within the physical device, rendering online attacks ineffective.
This offline signing process is precisely why hardware wallets are considered the top-tier solution for securing any significant crypto holdings.
How the Security Process Actually Works
The security behind a hardware wallet is built on a simple but brilliant workflow.
It all starts when you set up the device. It generates a seed phrase—a list of 12 to 24 random words—which acts as the master backup for all your private keys. This phrase is created offline and must be written down and stored securely; it should never touch an internet-connected device.
When you want to send funds, you create the transaction on your computer or phone using an app like Ledger Live or Trezor Suite. This unsigned transaction data is then sent to your hardware wallet.
The device shows the transaction details on its own trusted screen, asking you to physically confirm it by pressing a button. Once you approve, it signs the transaction internally using your private key and sends the signed data back to your computer to be broadcast to the network. Your keys never leave the hardware.
Picking the right device often comes down to personal preference, which coins you hold, and what features matter most to you. Our detailed hardware wallet comparison is a great place to start exploring the differences between top models. This layered security model—offline keys, a trusted display, and physical confirmation—is what makes these little devices a true fortress for your digital wealth.
Understanding Private Keys and Seed Phrases

To really get how hardware wallets work, we have to start with the two things they're built to protect: your private keys and your seed phrase. These are the bedrock of your crypto ownership. If you don't get this part right, nothing else matters.
Think of your crypto address on the blockchain as a digital vault. Your private key is the only key on earth that can open it. It's a long, messy string of random characters, and whoever has it holds absolute power over the funds inside.
Because that key grants total control, letting it fall into the wrong hands is the single biggest risk you face in crypto. If a hacker gets your private key, your assets are gone. It's that simple, and it's irreversible. This is precisely why hardware wallets exist—to create this key and then lock it down so no one can ever touch it.
The Role of Your Private Key
When you first set up your hardware wallet, it generates your private key. The crucial part? This all happens completely offline, inside the device's own secure little bubble. The key is born inside this digital fortress and is designed never, ever to leave.
So when you want to send some crypto, the wallet uses this internal key to mathematically "sign" the transaction, proving you're the one who authorized it. But the key itself never sees the light of day. It never touches your computer, your phone, or the internet.
This complete isolation is the core promise of a hardware wallet. It transforms your key from a vulnerable piece of data into a guarded, untouchable secret.
What Is a Seed Phrase?
Okay, so what if you lose your hardware wallet, or it gets stolen or just plain breaks? The private key is locked inside that now-useless device. Is your crypto gone forever?
Thankfully, no. This is where your seed phrase saves the day.
If a private key is the key to a single vault, the seed phrase (sometimes called a recovery phrase) is the master blueprint for rebuilding your entire set of keys from scratch. It’s a list of 12 to 24 simple, randomly generated words that can restore all your private keys on a brand-new device.
A seed phrase is your ultimate backup. It is the single most important piece of information you will own. With it, you can recover your entire crypto portfolio on any compatible wallet. Without it, losing your device means losing your funds forever.
This incredibly powerful backup is created during the same offline setup process. The device shows you the words one by one, and it becomes your job to write them down—on physical paper or metal—and store them somewhere ridiculously safe. For a more detailed look into how these phrases work, you can explore our guide on the wallet seed phrase for a deeper understanding.
Protecting Your Ultimate Backup
Here's the hard truth: your hardware wallet's security is only as strong as how well you protect your seed phrase. If someone finds that piece of paper, they don't need your device at all. They can just type those words into their own wallet and drain your accounts completely.
So, here are the non-negotiable rules for handling your seed phrase:
- Never Store It Digitally: Don't take a picture of it. Don't save it in a text file, email it to yourself, or put it in a password manager. Any digital copy is a target for hackers.
- Write It Down Physically: Use a pen and paper at a minimum. Even better, get a steel plate designed for seed phrases to protect it from fire or water damage.
- Store It Securely and Secretly: Hide your written phrase somewhere safe from theft, damage, or snooping eyes. Think a fireproof home safe or a bank's safe deposit box.
- Don't Say It Out Loud: Avoid reading your phrase aloud, especially when devices with microphones (like your phone or a smart speaker) are nearby.
- Verify Your Backup: Most hardware wallets have a feature to check if you wrote the phrase down correctly. Use it. Make sure every word is right and in the exact order.
Getting these two concepts down is essential to understanding hardware wallets. The device is the day-to-day bodyguard for your private keys, while the seed phrase is your doomsday recovery plan, putting the final responsibility for your wealth right where it belongs: in your hands.
Inside the Digital Fortress: Secure Elements and Firmware
So, what really makes a hardware wallet a fortress for your crypto? It’s not just that it’s offline. The real magic is in the specialized, purpose-built guts of the device working together to create an ironclad security bubble for your private keys. It all comes down to two things: the Secure Element and the device's firmware.
Think of a Secure Element (SE) as a tiny vault built inside the main vault. It's a dedicated, tamper-resistant chip specifically engineered to fend off seriously sophisticated attacks, both physical and digital. This isn't some newfangled tech; it's the same kind of high-security hardware used in passports, SIM cards, and premium credit cards to keep sensitive data locked down.
This little chip creates a completely isolated environment, walled off from the wallet's main processor. Your private keys are born there, they live there, and they sign transactions there. Critically, they can never leave the chip. It doesn't matter what's happening on your computer or even on the rest of the wallet's hardware—the keys are physically trapped inside.
The Role of the Secure Element Chip
The Secure Element is the ultimate bodyguard for your keys. Its entire reason for existing is to perform cryptographic gymnastics—like signing transactions—without ever letting the keys themselves see the light of day.
When you want to send a transaction, the unsigned data is passed into the Secure Element. The chip then uses your private key to sign it internally and only sends the finished signature back out. The key itself never moves, staying shielded from any malware, keyloggers, or spyware that might be lurking on your computer.
The Secure Element is what makes the "keys never leave the device" rule a physical reality. It's engineered to be a one-way street for cryptographic secrets, making it practically impossible for anyone to just rip the keys out of the hardware.
This hardcore hardware isolation is the bedrock of hardware wallet security and provides a level of protection that software alone could never hope to match.
Verifying Authenticity with Firmware Integrity Checks
While the Secure Element is busy guarding the keys, the device's firmware—its core operating software—needs its own protection. What's to stop a scammer from creating a counterfeit device that looks legit but runs malicious firmware designed to swipe your keys? This is where firmware integrity checks save the day.
Every single time you power on a genuine hardware wallet, it runs a cryptographic check to prove its firmware is authentic and hasn't been messed with. It’s basically asking itself, "Am I still running the official, secure software signed by my manufacturer?" If that check fails, the device will throw up a big warning or refuse to even boot, stopping a supply chain attack or tampered device dead in its tracks.
This quick boot-up verification gives you peace of mind that you’re dealing with the real deal, not some compromised clone.
A key fact about how hardware wallets function is their use of secure elements—tiny tamper-resistant chips like those in credit cards—that encrypt and isolate private keys from all external access. Devices like the Ledger Nano S Plus employ a certified EAL5+ secure chip, ensuring even if malware infects your PC, keys remain vaulted. During operation, the wallet verifies firmware integrity via a secure boot process before any signing, and many support multisig setups where multiple devices approve transactions, ideal for businesses. Discover more insights about hardware wallet market statistics on sqmagazine.co.uk.
These two components—a hardened chip and self-verifying software—form a powerful one-two punch. The Secure Element provides the physically isolated safe for your keys, while the firmware integrity check makes sure the guard at the door is always the one you trust. It's this combination that makes a hardware wallet such a formidable defense against a whole world of digital threats.
How Offline Transaction Signing Actually Works
This is where the real magic of a hardware wallet happens. Its entire security model is built around a slick, carefully designed process called offline transaction signing. Think of it as a multi-step verification dance that guarantees your private keys never touch the internet, even when you're sending crypto.
I like to compare it to a secret rubber stamp locked inside a tiny, impenetrable safe. To approve a document, you slide the paper through a slot, an internal mechanism stamps it, and the now-approved document slides back out. The stamp itself—your private key—never leaves the safe. This creates what we call an "air gap," a physical and digital barrier separating your keys from your vulnerable, internet-connected computer.
Let's walk through exactly how this works with a real-world example, like sending some Bitcoin to a friend.
Step 1: You Create the Transaction on Your Computer
First, you’ll open up the companion software on your computer or phone, like Ledger Live or Trezor Suite. This app is your command center for managing your crypto.
From here, you’ll kick off the transaction by entering three key details:
- The Amount: How much Bitcoin you're sending.
- The Recipient's Address: Your friend's public Bitcoin address.
- The Transaction Fee: How much you'll pay network miners to process it.
At this point, all you've done is create an unsigned draft of the transaction. It's just a set of instructions with no power behind it. It’s like writing a check but not signing it yet—it's worthless and can't be cashed. This unsigned data is completely safe to handle on your PC because it contains none of your secret info.
Step 2: The Software Sends the Unsigned Data to Your Wallet
Next, the app sends this unsigned transaction data over to your hardware wallet, which you’ve connected via USB or Bluetooth. This is just a one-way street for non-sensitive information; the app is basically just asking the wallet, "Hey, can you sign this for me?"
This step is so important because it shows the clear separation of duties. Your computer handles the nice user interface and talking to the internet. The hardware wallet is the dedicated, single-purpose security guard that handles the high-stakes approval.
Step 3: You Verify Details on the Trusted Display
This is probably the single most important security check in the whole process. The transaction details you typed on your computer screen now show up on your hardware wallet’s small, built-in trusted display.
The trusted display is your last line of defense against malware. If a virus on your PC secretly swapped your friend's address for a hacker's on your computer screen, the real hacker's address would still show up on your hardware wallet’s screen.
You need to meticulously check that the recipient address and the amount on the device’s screen perfectly match what you intended to send. Because the device's screen is totally isolated from your computer's software, it gives you a trustworthy, uncompromised view of what you're about to sign.
Step 4: You Physically Approve the Transaction
Once you've confirmed everything on the trusted display looks right, you give your final, physical consent. This means pressing one or two physical buttons right on the device.
This physical action is such a simple but powerful security feature. It proves that you, the human owner, are present and authorizing this exact transaction. Malware can’t press physical buttons, which stops a hacker from draining your funds remotely even if they’ve completely taken over your computer. It’s a deliberate, manual step that software alone just can't bypass.
Step 5: The Wallet Signs the Transaction Internally
Now for the main event. After you press the approval buttons, the hardware wallet takes the unsigned transaction data and uses your private key—safely stored inside its Secure Element chip—to create a unique digital signature.
This all happens entirely within the isolated, offline bubble of the hardware wallet. Your private key is used to do the math, but it's never revealed or sent anywhere. It stays securely locked inside its hardware prison, just like our rubber stamp in the safe.
Step 6: The Signed Transaction Is Sent Back
Finally, the hardware wallet sends only the new digital signature back to the software on your computer. Your private key stays put, as secure as ever.
The software then takes this signature, combines it with the original transaction details, and broadcasts the complete, fully authorized transaction to the Bitcoin network. From there, miners pick it up, confirm the signature is valid using your public key, and add it to the blockchain.
This elegant process is how hardware wallets provide such rock-solid security. By separating transaction creation from signing and demanding physical verification, they build a formidable wall around your most valuable digital secrets.
Connecting Your Wallet to Web3 and DeFi Apps
A hardware wallet is so much more than just a vault for your crypto. Think of it as your secure passport to the entire Web3 world. Whether you're jumping into DeFi, minting an NFT, or exploring a new dApp, your device is the key that lets you do it all without ever exposing your private keys. You get the best of both worlds: the smooth experience of a "hot" software wallet, but with the bulletproof security of cold storage.
The real magic happens when you pair your hardware wallet with an interface like MetaMask. Instead of storing your keys in your browser—which is a huge security no-go—you simply tell MetaMask to talk to your hardware wallet. This means MetaMask can build the transactions, but it has to hand off the final, all-important signing step to your offline device.
The Best of Both Worlds: Convenience and Security
This setup is a total game-changer. You can browse DeFi lending protocols, bid on NFT marketplaces, and interact with all sorts of Web3 platforms right from your computer. But when it's time to actually do something—like swap a token or buy some digital art—a prompt gets sent directly to your connected hardware wallet.
You see the transaction details on the device's own trusted screen and have to physically press its buttons to give the okay. Your hardware wallet signs the transaction inside its secure chip and sends only the signature back to MetaMask, which then broadcasts it to the network. Your private keys never, ever leave the device.
This flow diagram breaks down that core offline signing process that keeps you safe.
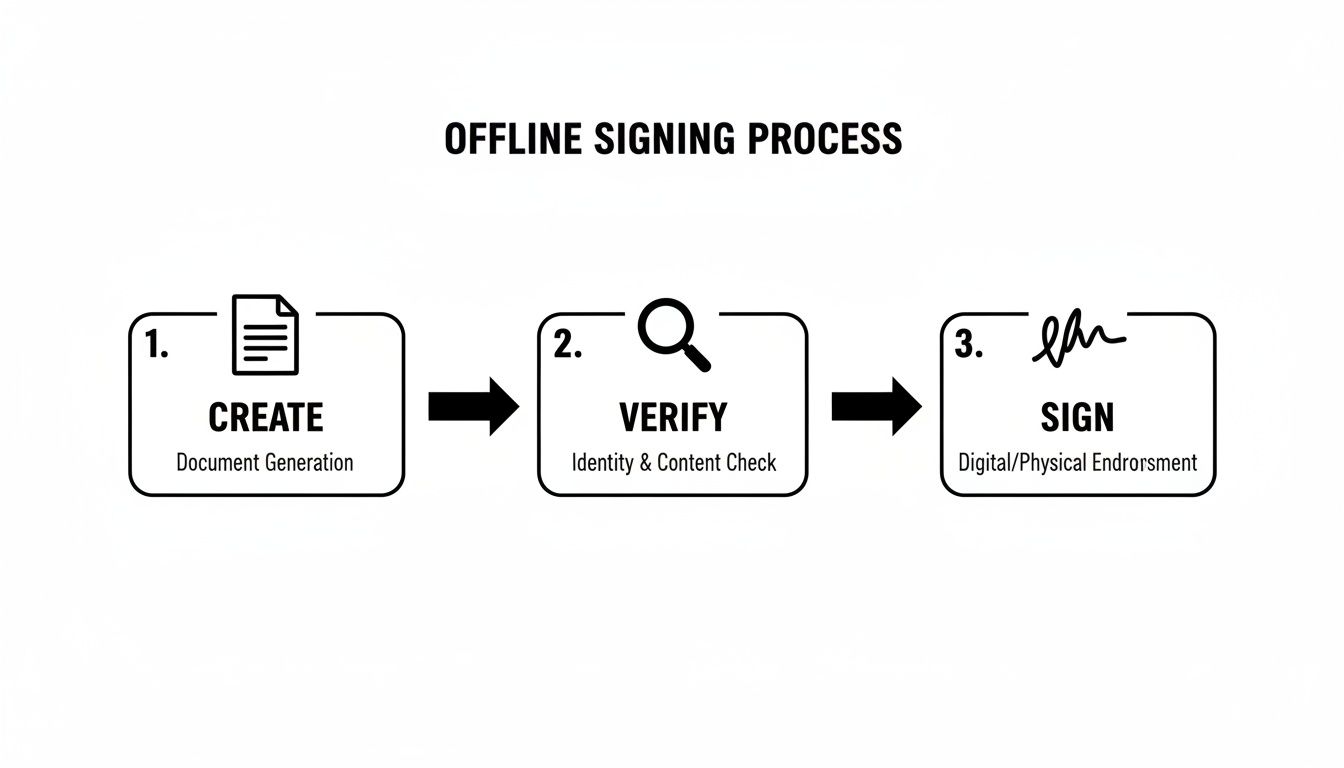
As you can see, the transaction is put together on your computer, but the critical signing happens on the offline hardware wallet. This physical separation is what prevents your keys from being exposed.
How Connectivity Works Without Compromise
Hardware wallets connect to your computer or phone with standard methods like USB or Bluetooth, allowing them to work with popular apps like MetaMask or Electrum. The crucial part is that the signing always happens entirely on the device. You review the critical details—the amount, the recipient address—on the wallet's screen before hitting "confirm" with its physical buttons. This adds a vital human verification step that stops many common attacks in their tracks. For more on the tech, you can check out overviews of the hardware wallet market.
By handing off signing authority to the hardware wallet, you're essentially turning a "hot" wallet like MetaMask into a secure, read-only interface. It becomes a messenger that can prepare transactions but has no power to approve them on its own, neutralizing the biggest risk of using browser-based wallets.
This process means that even if your computer was riddled with malware, a hacker is stuck. They can't remotely press the physical buttons on your device to authorize a transfer. It's a simple but incredibly powerful security model that lets you explore the wild world of Web3 with confidence, knowing your funds are protected by a physical barrier no remote attack can break.
A Few Common Questions About Hardware Wallets
Even after you get the hang of the tech, some practical questions always come up once you start using a hardware wallet day-to-day. What really happens if things go sideways? This last section tackles the most common worries head-on, giving you the confidence to use your device the right way.
What Happens If My Hardware Wallet Is Lost, Stolen, or Just Dies?
This is, without a doubt, the number one fear people have. But the answer is actually the most reassuring part of the whole system: if your hardware wallet is lost, stolen, or broken, your crypto is perfectly safe.
You have to remember, your funds aren't literally on the device. They exist on the blockchain. The wallet is just the ultra-secure key you use to unlock them. As long as you have your recovery seed phrase, you hold the master key to your digital assets.
Getting back in control is straightforward:
- Buy a new hardware wallet. It can be the same model or even one from a different, compatible brand.
- When setting up the new device, look for the option to "restore from recovery phrase" or something similar.
- Carefully type in your 12 or 24-word phrase in the exact right order.
And that's it. The new device uses that phrase to regenerate all of your private keys, and you'll have full access to your funds again. This is exactly why we say protecting your seed phrase is even more critical than protecting the physical device itself.
Is a Hardware Wallet Totally Immune to Every Attack?
While hardware wallets are the gold standard for crypto security, they aren't a magical forcefield against every conceivable threat. They are designed to defeat the most common attacks—remote hacks like malware, phishing, and spyware—and they do it with near-perfect reliability. But you still need to be smart about other, less common risks.
A supply chain attack, for example, is where a device gets tampered with before it even gets to you. This is why you must only buy your hardware wallet directly from the manufacturer or an officially authorized reseller. Never, ever buy one from a random seller on a marketplace. Real devices run firmware checks when they boot up precisely to catch this kind of meddling.
Then there's the physical threat, sometimes called a "$5 wrench attack," which is a grim way of saying you're physically coerced into giving up your PIN. A hardware wallet can't stop a real-world threat, but some devices have clever features like plausible deniability, letting you create hidden wallets with a separate passphrase.
A hardware wallet neutralizes the most widespread digital threats that steal crypto every day. But total security is always a team effort between good technology and smart user habits. Your own vigilance is a huge part of the equation.
At the end of the day, your single biggest point of failure is your seed phrase. If an attacker gets their hands on that piece of paper, they don't need your device or your PIN. They have everything they need.
Can I Use the Same Hardware Wallet for Different Cryptocurrencies?
Absolutely. Most modern hardware wallets from the big names like Ledger and Trezor are multi-currency devices. They're built from the ground up to securely manage the private keys for hundreds, or even thousands, of different coins and tokens all at once.
You'll use a companion app on your computer or phone, like Ledger Live or Trezor Suite, to see and manage your portfolio. From there, you can install little "apps" on your hardware wallet for each blockchain you want to interact with—one for Bitcoin, one for Ethereum, one for Solana, and so on.
Each app just helps the device speak the right language for that specific blockchain—generating the right kind of keys and signing transactions correctly. All the while, every single private key for every single asset remains completely isolated inside the device's secure chip.
Does My Hardware Wallet Need to Be Connected to the Internet?
This question really gets to the heart of the security model, and the answer is a very specific "yes and no."
-
The Hardware Wallet Itself: No. It is designed to be completely offline. It never connects to the internet. That's the whole point. Its only jobs are to generate your keys and sign transactions inside its own secure, isolated environment.
-
The Computer or Phone It’s Plugged Into: Yes. The software interface you're using (like Ledger Live) needs the internet to check your balances on the public blockchain and, crucially, to broadcast your signed transaction to the network so it can be confirmed.
Think of it as a two-part team. Your computer handles all the public-facing internet stuff, while your hardware wallet does all the secret, sensitive work completely offline. That "air gap" between them is what guarantees your keys are never exposed to online threats, even as you're sending a transaction.
If you've lost access to a wallet and need expert help navigating the recovery process, Wallet Recovery AI offers specialized services to restore control over your digital assets. Using advanced, secure techniques, we can help with forgotten passwords, corrupted files, and other access barriers for a wide range of wallets. Learn more and start your recovery process at walletrecovery.ai.


Leave a Reply