Losing access to your crypto wallet is a gut-wrenching experience, but what you do in the first few hours can make all the difference. It’s easy to panic, but a clear, methodical approach is your best bet. The goal is to figure out whether you're dealing with a simple access issue or a full-blown security breach, lock down any assets you can still reach, and document everything you know.
This initial response lays the groundwork for everything that follows.
Your First Steps After Losing Crypto Access
That sinking feeling when you can't get into your wallet or, worse, you see a zero balance—we've been there. Before you do anything else, take a breath. The moves you make right now are critical and will heavily influence whether you get your funds back. You need to shift from panic mode into a calm, problem-solving mindset. This isn't just about recovering what's lost; it's about protecting what's left.
First, you need to understand the nature of the problem. Is this a case of a forgotten password or a misplaced seed phrase? Or are you seeing the tell-tale signs of a malicious attack? The answer to that question dictates your next move. For instance, a password for an exchange suddenly not working could just be a login glitch. But if you spot unauthorized transactions, you're dealing with a security breach, and the clock is ticking.
Assess the Situation Calmly
You can't fix a problem you don't understand. Start by gathering every bit of information you have about the wallet and the last time you successfully used it. Don't jump to conclusions.
- Document Everything: Grab a pen and paper or open a secure note. Write down the wallet address, the type of wallet (e.g., MetaMask, Ledger, an exchange), the approximate amount of crypto, and the date you last accessed it.
- Identify the Cause: Try to retrace your steps. Did you forget a password? Did you lose a hardware device? Did you recently click on a suspicious link or download a weird file? Be honest with yourself.
- Check Transaction History: This is the most important step. Use a public blockchain explorer like Etherscan (for Ethereum) or Blockchain.com to look up your wallet address. Scrutinize the transaction history for any outgoing transfers you don't recognize. This is the fastest way to confirm if your funds were stolen or if they're simply inaccessible to you.
Secure Any Remaining Assets
If you have even the slightest suspicion of a security breach—like seeing a transaction you didn't authorize—your top priority is damage control. Assume your current computer, phone, or network is compromised.
You need to move any funds left in that wallet to a brand-new, secure one immediately. Create this new wallet on a completely different, trusted device if possible. This action is like quarantining your remaining assets, shielding them from whatever threat is active. Time is absolutely of the essence here; attackers often drain wallets in multiple stages.
The moment you suspect a compromise, the race against the attacker begins. Securing remaining assets isn't just a good idea—it's the only move that matters to prevent a total loss.
Set Realistic Expectations for Recovery
It's crucial to understand the odds to keep a level head. The hard truth is that not all lost crypto is recoverable, but many situations absolutely have a path forward. Simple access issues, like a forgotten password for a local wallet file, can often be resolved with the right recovery tools.
Recovering stolen funds, on the other hand, is a much tougher and more complex challenge. That said, the field of crypto recovery is evolving quickly. Recent data shows that recovery rates can be surprisingly high, depending on the specifics of the case. The process typically involves sophisticated blockchain forensics and sometimes cooperation with law enforcement, which have led to some major wins. For example, in one recent year, authorities managed to freeze over $300 million in scam-related crypto, proving that recovery is far from impossible.
Before you start any recovery attempt, it helps to know what you're up against. Here’s a quick-glance table to guide your immediate actions.
Immediate Actions for Different Crypto Loss Scenarios
This table summarizes the first steps you should take based on the most common ways people lose access to their crypto.
| Scenario | Immediate Action | Primary Goal |
|---|---|---|
| Forgotten Password | Gather all possible password clues (old notes, memory triggers). Prepare the encrypted wallet file for a recovery attempt. | Regain access through brute-force or memory-based recovery. |
| Lost Seed Phrase | Search all physical and digital storage locations where it might have been saved. Check for partial backups. | Find the complete, correct seed phrase to restore the wallet. |
| Hardware Wallet Lost/Damaged | Immediately purchase a new hardware wallet. Use your backed-up seed phrase to restore access to your funds. | Safely restore access to your assets on a new, secure device. |
| Unauthorized Transactions (Hack) | Move any remaining funds to a new, secure wallet on a clean device. Document the fraudulent transactions. | Prevent further losses and gather evidence for a potential recovery case. |
| Phishing Scam/Malware | Disconnect the compromised device from the internet. Run a full security scan. Change all critical passwords. | Contain the security breach and stop the attacker from gaining more access. |
Having this initial plan helps you react logically instead of emotionally. To get a better sense of what's achievable, you can learn more about crypto scam recovery statistics and their success rates to understand the modern landscape.
Before you call in the cavalry, it's worth trying everything you can on your own. I’ve seen countless cases where a situation that feels like a total loss is actually just a simple access problem you can solve yourself.
Let's walk through some of the DIY methods to get back into your crypto wallet. We'll start with the most obvious stuff—like trying to remember a password—before moving on to the heavy hitters, like using your seed phrase. The idea is to give you the tools to solve the most common lockouts. Stay calm, be methodical, and you might just find your crypto is well within reach.

Unlocking Your Own Vault with a Forgotten Password
It’s the most common reason people get locked out, and it's maddeningly simple: a forgotten password. We’re all human. But before you start looking for complicated recovery tools, let’s try to jog your memory. Our brains love patterns, even when we’re trying to be clever.
Grab a secure notebook or open a new, offline document. It's time to do a "brain dump" and list out every password variation you can possibly think of.
- Your Go-To Passwords: Start with the usual suspects. What passwords do you use for email, banking, or other high-security accounts?
- The usual modifications: How do you normally tweak them? Maybe you add a
123at the end, a!, or capitalize the first letter. Think about your habits. - Personal Details: Jot down important dates (birthdays, anniversaries), pet names, family names, old addresses—anything that might have made its way into your password.
- Common Mistakes: Don't forget to try common misspellings. You'd be surprised how often a simple typo is the real key.
Treat this like a structured brainstorming session. Work through your list and patiently try each one. I know it feels tedious, but this straightforward process works more often than you’d think. It's always the first thing you should do.
Finding and Using Your Seed Phrase or Private Keys
Your seed phrase is the master key to your kingdom. If you have those magical 12 or 24 words, you can almost always get your funds back, even if your computer explodes or you forget your password. The real trick is remembering where you stashed it.
Think back to the day you set up that wallet. Where did you write it down?
- Check your old notebooks, diaries, or planners.
- Look inside your safe, filing cabinet, or even a safety deposit box.
- Did you hide it inside a book on your shelf?
Maybe you took a risk and saved it digitally. It's not ideal, but many people do it.
- Search your computer and any backup drives for files named "recovery," "seed phrase," or "wallet backup."
- Check the secure notes section of your password manager.
- Dig through any encrypted cloud storage folders you might have used.
Critical Warning: Never, ever, ever type your seed phrase into a website or give it to someone claiming they can help. The instant you do, your wallet will be emptied. It happens in seconds.
Once you’ve found the phrase, getting your wallet back is usually pretty simple. You'll just need to download a fresh copy of the wallet software on a clean device and look for an option like "Import" or "Restore from seed phrase." Enter the words in the exact right order, and your crypto should be right there waiting for you.
Using Built-In Wallet Recovery Features
Most popular wallets are designed with disaster recovery in mind and have user-friendly functions built right in. While the core idea is the same across different wallets, the exact steps can vary. Knowing your wallet's specific process is crucial. You can see a list of wallets we've worked with over the years by checking our supported wallets at Wallet Recovery AI.
Let's run through a quick example.
Example: Restoring a MetaMask Wallet
Say your laptop dies and you need to get your MetaMask wallet running on a new one. Here’s what that looks like:
- Get the Official Extension: Head straight to the official MetaMask website and install the browser extension on your new machine.
- Choose to Restore: After it installs, MetaMask will give you two options: create a new wallet or import one. You want to "Import an existing wallet."
- Enter Your Phrase: This is the key step. You'll see a prompt to enter your 12-word Secret Recovery Phrase. Type each word carefully, with a single space in between, in the correct order.
- Set a New Password: Once your phrase is verified, MetaMask will ask you to create a new password. This password only protects this specific installation on this browser—it has nothing to do with your master seed phrase.
This same logic applies to hardware wallets like Ledger and Trezor. If you lose or break your device, you just buy a new one, punch in your 24-word recovery phrase during setup, and you're back in business. The crypto was never on the device anyway; it's on the blockchain. Your seed phrase is what proves you own it.
Using Advanced Tools for Password Recovery

When your own memory has failed you and the simple tricks haven't worked, it’s time to bring in the heavy machinery. This is where advanced software tools come into play, built specifically for the tough job of cracking passwords or piecing together a mangled seed phrase.
These aren't your typical apps. They are serious utilities that demand a bit of patience, some technical know-how, and an absolute focus on security. Think of yourself as a digital detective. You’ve got a locked safe—your wallet file—and a pile of clues based on what you remember about the password. These tools are the high-tech lockpicks that will test millions of combinations until one finally clicks.
This is often the last real step you can take before calling in a professional, and it can be surprisingly effective if you have even a faint idea of what the password looked like.
Diving Into Open-Source Recovery Software
For those comfortable getting their hands dirty, the open-source world has some incredibly powerful options. Two of the most respected tools out there are BTCRecover and Hashcat. They've earned trust because their code is completely public. Anyone can pop the hood and inspect it for backdoors or shady functions—a non-negotiable feature when you're dealing with private keys.
-
BTCRecover: This is a Python-based script made just for cryptocurrency wallets. It excels at dealing with common mistakes like typos, forgotten bits of a password, or incomplete seed phrases. You feed it your "best guess," and it cleverly applies a ton of variations—swapping letters, adding numbers, trying common symbols—to hunt for the right combo.
-
Hashcat: Often called the world's fastest password cracker, Hashcat is a more versatile beast that can tackle all sorts of encrypted files, not just crypto wallets. It puts your computer's graphics card (GPU) to work, letting it blast through password attempts at mind-boggling speeds. It’s a bit more complex to get running, but for raw power, it's hard to beat.
Let's be clear, though: these tools are not for beginners. You'll need to be comfortable with the command line and have a solid grasp of what you're doing. One wrong move in the setup could waste days of processing time or, far worse, put your data at risk.
The Brute-Force Method: A Game of Clues
The main strategy here is what’s known as a brute-force attack, but a smart one. Instead of just trying every character combination in the universe (which would take eons), you guide the software with a highly targeted list of possibilities. We call this a wordlist.
Creating a good wordlist is more of an art than a science. It’s all about digging into your memory and turning your habits into a simple text file the software can read.
- Start with a base list of every password piece you can remember.
- Toss in important names, dates, pet names, and old street addresses.
- Include common patterns you use, like adding
_2024or!to the end of your passwords.
The more accurate your clues, the faster this whole thing goes. If you recall your password was eight characters and started with "Crypto," you've just slashed the search time from impossible to potentially a few hours.
A targeted brute-force attack isn't about random guessing. It's about methodically testing every plausible variation of what you already partially know. The quality of your input is everything.
Security First: Your Offline Recovery Fortress
I cannot stress this enough: you must run these recovery tools on a computer that is completely disconnected from the internet. The second you load your encrypted wallet file onto a connected machine, you're opening the door to malware, keyloggers, and spyware just waiting to snatch your crypto the moment it's unlocked.
Here’s a simple security protocol to follow religiously:
- Prep an Offline Machine: Grab a spare laptop or an old computer you can take offline. Disconnect it from Wi-Fi and unplug any network cables. For an extra layer of security, boot it up using a fresh Linux USB drive.
- Transfer Files Securely: Use a clean, freshly formatted USB stick to copy the recovery software (like BTCRecover) and your encrypted wallet file over to the offline machine.
- Run the Recovery: Let the software do its thing entirely on the isolated computer. This could take hours or even days, depending on the password's complexity and your computer's power.
- Access and Move Your Funds: If it works, use that same offline machine to open the wallet, create a new transaction, and send the funds to a brand-new, secure wallet you've already set up. Only after the funds are safe should you even think about reconnecting that computer to the internet.
Following these steps ensures that even when your wallet is briefly unlocked, your private keys never touch the open internet. Learning how to recover lost cryptocurrency safely is just as critical as the recovery itself.
When to Hire a Professional Crypto Recovery Service

You’ve tried everything. You’ve retraced your steps, run every tool you can think of, and scoured old hard drives, but you’re still locked out. That feeling of hitting a wall is frustrating, but it’s not the end of the road. It just means you might need a different kind of key.
This is the point where bringing in a professional crypto recovery service makes sense. These aren't just last-ditch efforts; they are specialized interventions designed for complex, high-stakes problems that go way beyond what DIY solutions can handle.
Knowing when to make that call is half the battle. If your crypto was stolen in a sophisticated hack, laundered through a confusing maze of transactions, or is stuck in a corrupted wallet file, you're probably out of your depth. Trying to fix these issues on your own can sometimes make things worse by muddying the very digital trail an expert needs to follow.
Identifying Scenarios That Demand an Expert
Look, not every locked wallet needs a team of pros. But for certain high-complexity situations, they're often the only realistic path forward. It’s time to call for backup when you're facing problems that are a lot more complicated than a simple forgotten password.
Think about these specific situations:
- Sophisticated Hacks and Thefts: If your funds were actively stolen and you can see them moving on-chain, time is absolutely critical. Experts use forensic tools to trace these funds in real-time, hoping to spot when they land at a centralized exchange where they can be frozen.
- Complex Scams: Investment scams, elaborate phishing schemes, and social engineering attacks often involve washing stolen assets through multiple wallets and privacy tech like coin mixers. Unraveling that tangled web is a job for specialized software and serious expertise.
- Technically Damaged Wallets: Sometimes, the problem isn't your password but the wallet file itself. Data corruption, hardware failure, or weird issues with non-standard wallet formats can make a wallet completely inaccessible, even if you have the right credentials.
- Large Value at Stake: If the amount of crypto at risk could change your life, the cost of a professional service becomes a calculated investment. You have to weigh the service fee against the total value of what you stand to get back.
Professional crypto recovery services exist to tackle the unique challenges of blockchain technology. While decentralized and secure, the blockchain offers very little recourse when your assets are gone. These firms work to get them back through advanced tracing, deep wallet analysis, and even collaboration with law enforcement. In a recent year, just one prominent firm recovered over $715 million, showing just how effective this approach can be. You can learn more about how top crypto recovery services operate in 2025 and see the kind of results they achieve.
Demystifying the Professional Recovery Process
So, what do these services actually do? It's a whole lot more than just running a password cracker on a supercomputer. Their process is methodical and multi-faceted, combining powerful technology with human expertise to attack the problem from every angle.
The image below gives you a glimpse into the kind of in-depth analysis and discussion that goes on inside these firms as they work through a complex case.

This screenshot highlights a community discussion about a leading recovery firm, Puran Crypto Recovery, which underscores just how important reputation and a proven track record are in this high-stakes field.
A legitimate recovery service will never promise a 100% success rate. They will give you a realistic assessment based on the facts of your case, clearly explaining the challenges and the strategies they plan to use.
Their toolkit is extensive and includes a range of actions you simply can't do on your own.
Key Professional Services
| Service | What It Involves | When It's Used |
|---|---|---|
| Blockchain Forensics | Using analytical software to trace the flow of stolen crypto across different blockchains, wallets, and exchanges. | Cases of theft, scams, and unauthorized transactions. |
| Law Enforcement Liaisons | Compiling evidence into a formal report and working with authorities to issue subpoenas or freeze assets at regulated entities. | When stolen funds land at a known, compliant exchange. |
| Advanced Decryption | Applying massive computational power to brute-force complex passwords or repair corrupted wallet files. | Forgotten passwords for high-value wallets or damaged files. |
| Vulnerability Exploits | In rare cases, ethically exploiting a flaw in a wallet's software to regain access (with full client permission). | Highly technical cases involving obsolete or faulty software. |
Hiring a professional is a big decision. It means trusting a third party with sensitive information for a shot at getting your assets back. The key is to make an informed choice based on a clear understanding of when their help is not just an option, but a necessity.
Choosing a Legitimate Recovery Expert and Avoiding Scams
When you’re in a panic over lost crypto, you're a prime target. The space is, unfortunately, crawling with scammers ready to prey on that desperation. They promise the moon, take your money, and leave you worse off than before. Getting through this means taking a breath and learning what real, professional help actually looks like.
The number one rule? Slow down. Scammers love to create a sense of urgency, pushing you to make a bad decision quickly. A genuine expert gets it. They’ll be methodical and transparent, never pressuring you into a snap judgment.
Vetting Potential Recovery Services
Your main job here is to sort the pros from the predators. That means doing some real digging and not just taking a flashy website at its word. You have to verify everything.
A good starting point is to check for community feedback. Dive into forums like Reddit or Bitcointalk and search for the company's name. You're looking for real, detailed reviews—the good and the bad. A service with absolutely no online footprint is just as sketchy as one with a hundred generic five-star reviews that all sound like they were written by the same person.
You should also look for signs of a real, professional operation. A legitimate business will have:
- A clear pricing model. Most credible services work on a contingency basis, meaning they take a percentage after your funds are successfully recovered.
- A provable track record. They should be able to point to case studies or at least share anonymized success stories.
- A public-facing team. Anonymity is a massive red flag. You should be able to find their key people on professional networks like LinkedIn.
This infographic gives you a quick breakdown of what you can generally expect from different recovery methods in terms of success and cost.
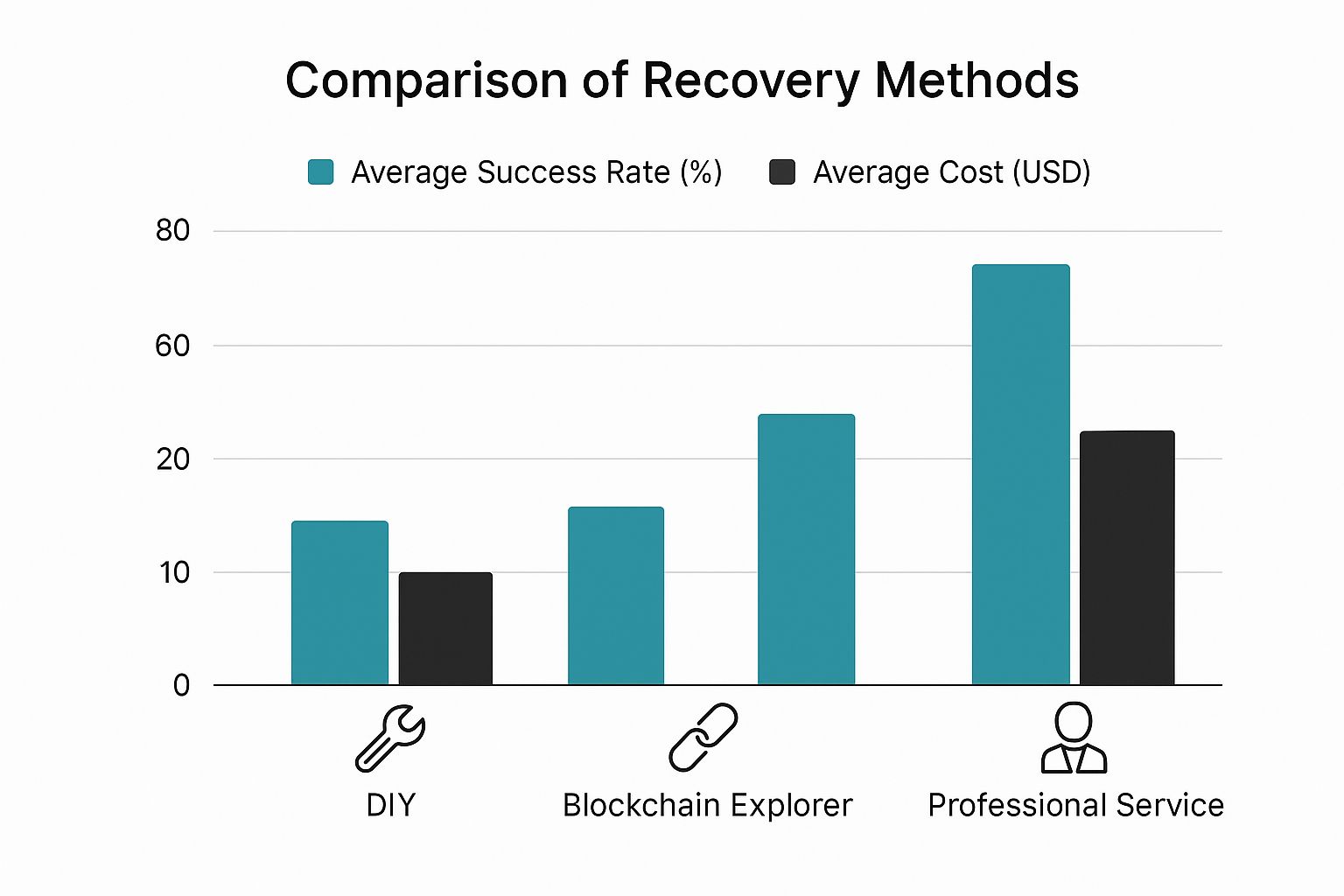
As you can see, professional services come with a higher price tag, but they also give you a much better shot at success, especially when things get complicated.
Red Flags That Scream Scam
Scammers tend to use the same old playbook. Once you know their moves, you can protect yourself from becoming just another statistic. If you see any of these signs, it's time to run.
The biggest giveaway is a demand for upfront payment. A scammer's entire model is built around getting your money before they vanish. They’ll call it a "tax," a "processing fee," or a "software license," but it’s always a trick.
A legitimate crypto recovery expert’s compensation is tied directly to their success. If they aren’t confident enough in their own abilities to work on a contingency basis, why should you be?
Another classic tactic is the impossible guarantee. Anyone promising a 100% success rate is flat-out lying. The process of how to recover lost cryptocurrency is full of variables. An honest professional will give you a realistic assessment of your odds, not a fairy tale.
To make it even clearer, here’s a quick comparison to help you spot the difference between a real pro and a fraud.
Legitimate Recovery Service vs Recovery Scam
This table breaks down the key characteristics that separate trustworthy experts from the scammers you need to avoid.
| Characteristic | Legitimate Service | Scam Operation |
|---|---|---|
| Payment Structure | Primarily contingency-based (a percentage of recovered funds). | Demands large upfront fees before any work is done. |
| Guarantees | Provides a realistic assessment of success probability. | Promises a 100% success rate or guaranteed results. |
| Anonymity | Has a public team, verifiable address, and professional online presence. | Uses anonymous agents, fake names, and has no physical address. |
| Communication | Professional, transparent, and patient. Willing to answer all questions. | High-pressure tactics, vague answers, and creates a false sense of urgency. |
| Process | Explains their methodology and keeps you informed of progress. | Process is a "black box"; they refuse to explain how they work. |
At the end of the day, picking a recovery partner is all about trust and verification. Take your time, ask the tough questions, and never send money or private info until you're absolutely sure you’re working with a credible organization like Wallet Recovery AI.
Protecting Your Crypto Assets Moving Forward
Successfully getting your crypto back is a massive relief, but let’s be honest—it’s an experience that leaves a mark. The real win isn't just recovering your funds; it's about building a fortress around them so you never have to go through that stomach-dropping panic again.
Now we shift from recovery to prevention. Think of this as your personal security upgrade. It’s not about becoming paranoid. It’s about being smart and deliberate with a few key actions that will dramatically lower your risk. A couple of simple changes can be the difference between a secure portfolio and a future disaster.
Reinforce Your Seed Phrase Storage
Your seed phrase is the ultimate master key. How you protect it is, without a doubt, the single most important security decision you'll ever make.
Most people just scribble it down on a piece of paper and tuck it into a drawer. That's a common approach, but it’s incredibly fragile. It's an open invitation for fire, water damage, or theft to wipe you out.
It's time to adopt the gold standard for seed phrase security.
- Go Analog and Offline: Never, ever store your seed phrase on a computer, in a cloud drive, or in a password manager. Digital storage is a massive, glowing target for hackers.
- Use Metal Plates: Get your phrase stamped or etched onto a fireproof, corrosion-resistant metal plate. This little piece of metal can survive almost anything you throw at it.
- Split the Location: For the highest level of security, consider splitting your seed phrase into two or three parts. Store each piece in a separate, secure location—think a safe deposit box, a safe at home, and maybe with a trusted family member.
This might sound a bit extreme, but it guarantees that no single disaster—a house fire, a flood, or a break-in—can compromise your access.
Proactive security isn't a one-time setup; it's an ongoing mindset. The habits you build today are the shield that protects your assets tomorrow.
Embrace Hardware Wallets and Best Practices
If you're still holding a significant amount of crypto on an exchange or in a software wallet (a "hot wallet"), it's time to graduate. A hardware wallet is a purpose-built device that keeps your private keys completely offline, making it virtually impossible for hackers to get to them remotely.
Think of it as a personal vault for your crypto. Even if your computer is riddled with malware, your funds stay safe because every transaction has to be physically confirmed on the device itself. For anyone serious about long-term crypto security, this is non-negotiable.
Beyond the hardware, you need to weave these security habits into your daily routine:
- Enable Multi-Factor Authentication (MFA): Ditch SMS-based 2FA. It's too vulnerable to SIM-swap attacks. Instead, use an authenticator app like Google Authenticator or, even better, a physical security key like a YubiKey.
- Whitelist Addresses: On exchanges, take a minute to set up address whitelisting. This creates an "approved" list of wallets you can send funds to, stopping a hacker from draining your account into their own pocket.
- Practice Constant Vigilance: The threats are always evolving. Stay up to date on the latest phishing scams and social engineering tricks. Be deeply suspicious of unsolicited emails, DMs offering "help," or urgent messages asking you to verify your wallet. Always, always verify information through official channels.
By layering robust physical security for your seed phrase with the digital armor of a hardware wallet and smart daily habits, you build a multi-layered defense. This approach helps ensure that your recent experience needing to recover lost cryptocurrency remains a one-time event.
A Few Common Questions About Crypto Recovery
Even with a detailed guide, you've probably got some questions buzzing around. Let's tackle a few of the most common ones we hear, giving you some straight answers to help you move forward with a bit more clarity.
Is It Actually Possible to Recover Stolen Cryptocurrency?
The short answer is yes, it's possible—but it’s never a simple task. Success isn't guaranteed and really depends on a few key things: how fast the theft gets reported, where the criminals sent the funds, and the tactics they used to cover their tracks.
Recovery usually means digging into some serious blockchain forensics to trace the stolen assets. If we get lucky and the crypto lands in a wallet at a major exchange that requires customer ID (KYC), there's a real shot that law enforcement can get involved and freeze the account. The trail goes cold fast, though, if the funds are run through coin mixers or other privacy tools, which makes recovery incredibly difficult.
How Much Do Crypto Recovery Services Typically Cost?
The cost for professional help can vary quite a bit. Most legitimate services, including us, work on a contingency fee basis. Plain and simple, this means you don't pay us unless we successfully get your funds back.
This fee is just a percentage of whatever we recover for you, usually somewhere between 10% and 30%. The final rate really comes down to how complex your specific case is, the amount of crypto we're talking about, and the resources needed to get the job done.
Be very, very careful of any service asking for a big payment upfront. A small fee for an initial assessment might be normal, but the main payment should always be tied to success. It keeps everyone on the same side.
What Should I Do If I Sent Crypto to the Wrong Address?
This is easily one of the most heartbreaking situations in crypto because blockchain transactions are irreversible. That's a feature, not a bug. Once a transaction is confirmed, there's no "undo" button.
If you send funds to the wrong address, your options are pretty slim. Unless you personally know who owns the receiving wallet and can convince them to send it back, the crypto is almost certainly gone for good. If it's an invalid address that no one can access, those funds are now permanently locked away from everyone.
This is why we're always preaching about diligence. Double-check, then triple-check every single character of a recipient's address before you confirm anything. For an extra layer of safety, a lot of wallets and exchanges have an address whitelisting feature, which is a fantastic tool for preventing these kinds of costly errors.
For more in-depth answers to specific questions, you can find a ton of information by exploring our comprehensive FAQ page.
Trying to navigate the maze of wallet recovery can feel overwhelming, but you don't have to go it alone. Wallet Recovery AI blends deep expertise with advanced tech to help people like you get back into their accounts safely. If you’re ready to see what's possible, let our team take a look at your situation. Start your confidential recovery process today.
Article created using Outrank


Leave a Reply