Think of your crypto recovery phrase as the one and only master key to your entire digital fortune. It's a list of 12 or 24 simple words that can bring your entire crypto portfolio back to life on any new device if you lose your old one. This phrase is your ultimate safety net, the one thing that can restore your assets if your phone gets stolen or your laptop dies.
The Ultimate Master Key to Your Crypto
In the regular banking world, forgetting your password is no big deal. You click "Forgot Password," answer a question, and you're back in business. But crypto is different. It’s decentralized, which is a fancy way of saying there's no customer service hotline to call and no one to reset your password. You are your own bank, which means security is 100% on you.
This is where your crypto recovery phrase becomes the single most important piece of information you will ever own.
It's not just a password—it's the actual blueprint for your wallet. When you have this phrase, your wallet can mathematically regenerate every single private key you need to access and spend your funds. It's the root from which everything else grows.
The Stakes Are Incredibly High
Losing this master key is catastrophic. If it's gone, any crypto tied to that wallet is locked away forever, out of reach for you and everyone else. This isn't just a "what if" scenario; it's a real, multi-billion-dollar problem.
The nightmare of a lost phrase has been around since the beginning. Analysts from Ledger estimate that by early 2025, somewhere between 2.3 million and 3.7 million Bitcoin (BTC) will be permanently lost because of forgotten passwords or misplaced recovery phrases. At projected 2025 prices, that's a mind-boggling $207 billion to $370 billion just gone. Vanished. You can learn more about the scale of lost Bitcoin from AInvest.
Your crypto recovery phrase is the only thing standing between you and the permanent loss of your digital assets. Treat it with the same seriousness you would the deed to your house or the keys to a physical vault.
This idea of self-custody is what makes crypto so powerful, but it also means the responsibility is entirely yours. In the next sections, we'll break down exactly how this phrase works and, more importantly, how to keep it safe from all the common threats. Let's make sure you never become another statistic in the digital graveyard of lost funds.
Crypto Recovery Phrase Key Concepts at a Glance
For those just starting out, wrapping your head around this concept is crucial. This table breaks down the most important ideas into simple terms.
| Concept | What It Means for You | Analogy |
|---|---|---|
| Self-Custody | You, and only you, have full control over your funds. No bank or third party can access them without your keys. | You're not just a customer of the bank; you are the bank. You hold the keys to the vault. |
| Recovery Phrase | The 12 or 24 words that act as your master backup. It can restore your entire wallet on a new device. | It’s like the master combination to a safe. As long as you have it, you can always get inside. |
| Private Keys | The individual "keys" that sign off on transactions for each specific crypto asset in your wallet. | Think of these as the individual keys to different safe deposit boxes inside your main vault. |
| Irreversibility | Once you lose your recovery phrase, it's gone forever. There is no "forgot password" option to get it back. | If you drop the master key to your vault into the ocean, it’s gone for good. The vault stays locked. |
Understanding these four points is the foundation of keeping your crypto safe. Everything we'll discuss builds on this fundamental reality: in crypto, you are in charge of your own security.
How Your Recovery Phrase Actually Works
To really get why your crypto recovery phrase is so important, we need to peek behind the curtain. It’s not just a random jumble of words; it’s the result of a very precise, universally accepted cryptographic process. This system is what allows a simple list of words to securely control billions of dollars in assets all over the world.
The whole thing is built on an industry standard called BIP39. Think of BIP39 as the universal recipe book for making crypto wallets. It lays out the exact rules for how a wallet takes pure randomness and turns it into that memorable 12 or 24-word phrase you've carefully written down.
And because nearly every modern wallet follows this same recipe, your phrase becomes incredibly portable. You can take a phrase generated by one wallet and use it to bring your funds back to life on a completely different one, as long as they both speak the language of BIP39.
From Randomness to Words
The journey from nothing to a powerful master key starts with one critical ingredient: entropy.
Entropy is just a fancy word for pure, unpredictable randomness. Your wallet software creates this randomness, which is really just a very long string of ones and zeros. This unique digital fingerprint is what guarantees no two recovery phrases on Earth are ever the same.
This initial string of randomness is then run through the BIP39 process:
- Generate Entropy: The wallet creates a random number, usually 128 or 256 bits long.
- Create a Checksum: A small piece of that data is tacked onto the end to act as an error-checker. This little trick helps make sure you've entered your phrase correctly when you’re trying to recover your wallet.
- Map to Words: The long binary string is then chopped up into 11-bit chunks. Each chunk corresponds to a specific number between 0 and 2047.
- Select from the Wordlist: Each number is then matched to a word on the official BIP39 wordlist, which contains exactly 2,048 carefully chosen words.
The specific words you get, and their exact order, are a direct result of that initial random number. This is why the sequence is everything. Changing just one word or swapping the order of two will point to a completely different—and almost certainly empty—wallet.
If you're curious to see how those bits and words connect, a tool like this mnemonic code converter can help you visualize the technical magic behind your phrase.
Your Phrase as Financial DNA
The best way to think about your crypto recovery phrase is as your financial DNA. Just like your unique DNA sequence holds the complete blueprint to build you, your recovery phrase holds the master blueprint to generate every single private key your wallet will ever need.
From this one phrase, your wallet can mathematically derive an almost infinite number of private keys. This is why you can receive Bitcoin, Ethereum, and other assets to different addresses all within the same wallet—they all sprout from that single master seed.
This concept map shows how your recovery phrase acts as the central master key, unlocking both access to your wallet and total control over your assets.
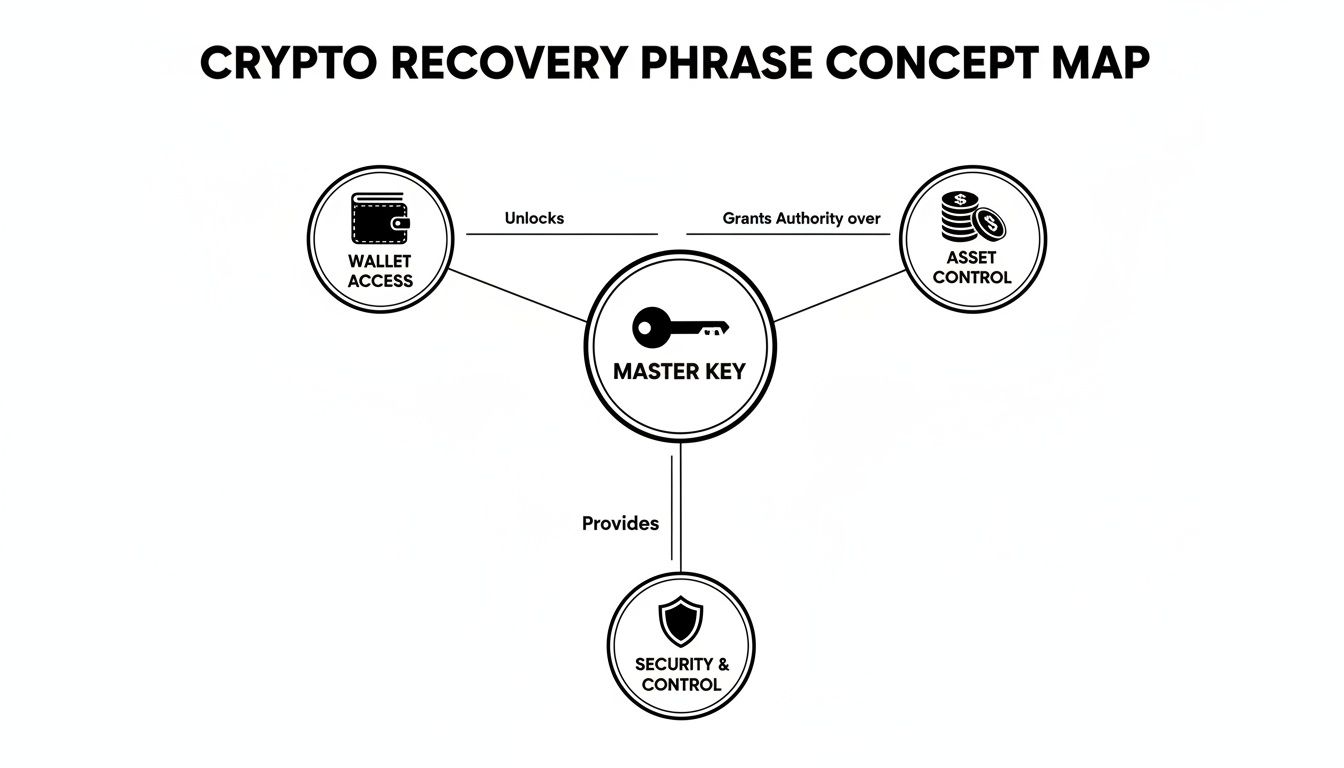
As you can see, the master key—your recovery phrase—is the single point of origin for everything your wallet does, from simply opening it up to having complete control over every coin you hold.
The Real-World Dangers to Your Recovery Phrase
Knowing what a recovery phrase is and why it's powerful is one thing. Understanding just how easily you can lose it all is another. These aren't just far-off, theoretical risks; they are active threats that exploit simple human mistakes and digital blind spots every single day. If you want to protect your assets, you have to get real about what you're up against.
We can split these threats into two main camps: digital attacks that come at you through your screen and physical risks that happen right in your own home. Both can wipe out your wallet in a blink if you're not paying attention. Let's break down exactly how these attacks work and the simple accidents that can cost you a fortune.
Digital Threats Lurking Online
In the digital world, attackers use clever tricks and nasty software to fool you into handing over your recovery phrase. Their methods are getting more sophisticated all the time, designed to look so real that they can catch even the most careful person off guard.
One of the oldest and most effective tricks in the book is phishing. It might start with an email or a direct message that looks like it's from your wallet provider or a crypto exchange. The message will create a sense of panic—"your account is at risk!" or "urgent verification required!"—and push you to a fake website that's a perfect clone of the real one. The second you type your recovery phrase into their look-alike site, it's game over. Your funds will be gone in minutes.
Then there's the outright malicious software to worry about. This stuff can sneak onto your devices in a number of ways:
- Keyloggers: This is malware that silently records every single thing you type. If you ever type your recovery phrase into a compromised device, the keylogger captures it.
- Clipboard Hijackers: A sneaky bit of code that watches what you copy and paste. If you ever copy your phrase to move it somewhere (don't do this!), this malware can snatch it right from your clipboard.
- Fake Wallet Apps: Scammers create convincing counterfeit versions of popular crypto wallets and sneak them into official app stores. You download what you think is the real deal, enter your phrase to "restore" your funds, and instead, you're just handing the keys directly to a thief.
- Malicious Browser Extensions: Some browser add-ons ask for way too many permissions, letting them read data from the websites you visit. A purpose-built malicious extension could be designed to do one thing: find and steal recovery phrases entered into web wallets.
Let's make this crystal clear: your recovery phrase should never be typed, photographed, saved as a note, or stored on any device that has ever touched the internet. Think of it as being radioactive to all things digital.
The amount of money lost to these kinds of attacks is staggering. Compromised recovery phrases and private keys are the fuel for some of the biggest heists in history. By mid-July 2025, hackers had already siphoned $2.17 billion from crypto services. To put that in perspective, that's more than the $2.2 billion stolen in all of 2024—a shocking 99% jump in just six months. According to research from Deepstrike.io, it marks the worst first-half performance since tracking began.
Physical Risks in the Real World
While digital schemes are cunning, don't forget that the physical security of your phrase is just as vital. After all, it’s often just a simple piece of paper, making it vulnerable to everyday dangers that have nothing to do with hackers.
The most straightforward threat is theft. If you just tuck your phrase into a desk drawer, a burglar could stumble upon it and gain immediate, unrestricted access to your crypto. Unlike a stolen laptop that might be password-protected, a piece of paper with 12 or 24 words on it is an instant jackpot for a thief.
But beyond outright theft, you have to plan for simple accidents and bad luck:
- Fire or Water Damage: A house fire or a burst pipe could easily destroy a paper backup, leaving you with absolutely nothing.
- Accidental Disposal: It’s just a piece of paper. You, a family member, or a cleaner could easily mistake it for junk and toss it in the trash.
- Fading and Deterioration: Over time, ink fades and paper degrades. The one day you desperately need it, you might find the words have become completely unreadable.
Securing your recovery phrase means fighting a war on two fronts. You need to be just as vigilant against a clever phisher as you are against the simple, unpredictable chaos of the real world.
Best Practices for Securely Storing Your Phrase

Knowing the threats is one thing, but acting on them is what really protects your crypto. A crypto recovery phrase scribbled on a sticky note and left on your desk is basically an open invitation for someone to walk away with your funds.
The fundamental rule of secure storage is simple but absolutely non-negotiable: keep it offline, make it durable, and build in redundancy. This isn't just about hiding it well; it's about creating a system so tough it can survive theft, fire, floods, and even your own forgetfulness. Let's dig into the real-world strategies that work.
Go Analog and Fireproof Your Phrase
Your first and most powerful move is to get your recovery phrase out of the digital world entirely. As soon as you do this, you've instantly immunized yourself against a whole class of threats like malware, remote hackers, and phishing attacks.
But a simple piece of paper is flimsy. It can get wet, fade, or turn to ash in a fire. To truly fortify your backup, you need to think in terms of physical permanence. This is where metal storage solutions come in—they're engineered to be fireproof, waterproof, and crush-proof.
You have a few great options here:
- Metal Plates: You can stamp or etch your 12 or 24 words onto thick plates of stainless steel or titanium. The result is a nearly indestructible record of your master key.
- Capsule Devices: These are small, tough cylinders that hold individual tiles for each word of your phrase. They're compact, discreet, and incredibly durable.
- Steel Wallets: These are often card-sized devices where you assemble your phrase using letter tiles, creating a permanent backup that's easy to store.
These methods transform your fragile string of words into a physical artifact built to last. For a deeper dive, check out this guide on the best metal seed phrase storage to find a device that fits your security needs and budget.
When it comes to keeping your recovery phrase safe for the long haul, not all storage methods are created equal. You need to balance security against durability and convenience. Here's a quick comparison of the most common approaches.
Recovery Phrase Storage Methods Compared
| Storage Method | Security Level | Durability | Best For |
|---|---|---|---|
| Paper Wallet | Low | Very Low | Quick, temporary backups only. Not for long-term storage. |
| Digital File (Unencrypted) | Very Low | High | Never recommended. Extremely vulnerable to malware and hacks. |
| Digital File (Encrypted) | Medium | High | Tech-savvy users who understand encryption and key management. |
| Metal Storage | High | Very High | Long-term, "deep cold" storage for significant holdings. |
| Splitting/Shamir's Secret | Very High | Depends on method | Advanced users securing large amounts against multiple threats. |
| Safe Deposit Box | High | High | Users who trust a third-party institution for physical security. |
Ultimately, a fireproof metal device stored offline offers the best combination of security and resilience against physical threats.
Implement Geographic Separation and Redundancy
Never, ever rely on a single copy of your recovery phrase, no matter how tough your storage method is. A single point of failure is a massive risk. Creating multiple backups and stashing them in different, secure physical locations is a strategy known as geographic separation.
Think it through: if your only backup is in a home safe, what happens during a targeted burglary or a house fire? Your assets could be gone for good. By spreading your backups out, you eliminate that risk.
The core idea is that no single disaster can wipe out all copies of your recovery phrase. One copy might be in your home safe, another in a bank’s safe deposit box, and perhaps a third with a trusted family member in another city.
This creates a resilient system. If one location is compromised, you still have a way to access your wallet and move your funds to safety.
Use Splitting and Multi-Signature Setups
If you're protecting significant wealth, you might want to level up your security with more advanced techniques. One powerful method is to split your recovery phrase into several parts.
For instance, you could break a 24-word phrase into three segments of eight words each. You would then store each piece in a separate, secure location. A thief would need to find all three pieces to reconstruct the phrase, making their job exponentially harder.
An even more robust solution is a multi-signature (multisig) wallet. A multisig setup requires approvals from multiple private keys before any transaction can be sent. A common setup is a 2-of-3 wallet, which means two out of three designated keys must sign off on any transaction.
This completely demolishes the concept of a single point of failure. Even if an attacker steals one of your keys, they can't do anything with it. While setting up a multisig wallet is more involved, it provides a professional-grade security model that is nearly impossible to breach.
Here's the rewritten section, crafted to sound like an experienced human expert:
How to Restore Your Wallet With a Recovery Phrase
This is where the magic happens. That list of words you wrote down and stored safely? It's about to become your lifeline. Let’s say your phone gets lost, stolen, or just gives up the ghost. It’s a stressful situation, for sure, but this is exactly what your recovery phrase was designed for. It proves your crypto is tied to you and your phrase, not to any one phone or laptop.
Let's walk through exactly how you'd bring your wallet back to life on a brand-new device. You’ll see just how powerful those simple words really are.
Step 1: Find and Download the Official Wallet App
First things first, and this is non-negotiable: you absolutely must download the legitimate, official wallet app. The crypto world is full of scammers who build pixel-perfect fake apps just to trick you into handing over your recovery phrase.
- Go Straight to the Source: Always start by going directly to the wallet’s official website. For example, type
MetaMask.ioorTrustWallet.cominto your browser yourself. - Use Their Links: Once you're on the official site, use their download links. They'll point you to the correct, verified app in the Apple App Store or Google Play Store.
- Do a Sanity Check: The real app will have a long history, probably with thousands of reviews and a huge number of downloads. If you see an app with just a handful of users, that's a massive red flag.
Whatever you do, don't just search for the wallet in an app store. You'd be surprised how easily a convincing-looking fake can pop up in the search results.
Here’s a look at the official MetaMask website. Notice how they give you clear, direct download buttons.
Starting from the official website like this is the single best way to know you're getting the right software.
Step 2: Kick Off the Import Process
Okay, you’ve got the verified app installed on your new, clean device. Fire it up. You'll almost always see two main choices: "Create a New Wallet" or an option to import an existing one.
You’re restoring, so you want to import. The button might say something like "Import using Secret Recovery Phrase," "Restore Wallet," or "I already have a wallet." This tells the app you’re bringing your own master key to the party.
Step 3: Carefully Enter Your Recovery Phrase
This is the most sensitive part of the whole process. The app will show you a text box, ready for your 12 or 24-word recovery phrase.
Time for a Security Check. Do this somewhere private. Make sure no one is looking over your shoulder and no security cameras can see your screen. Double-check that you're on a secure, private Wi-Fi network—not the free Wi-Fi at a coffee shop or airport.
Enter each word one by one, in the perfect order, with a single space separating them. Spelling counts. Order is everything.
Most wallets will then ask you to set a new password. This password is just for convenience—it locks the app on that specific device so you don't have to type the full phrase every time you open it. It does not replace your master recovery phrase.
Once you’ve entered the phrase and set your new password, the wallet software gets to work. It uses the underlying BIP39 standard to instantly regenerate all your private keys from that phrase. A moment later, your wallet should appear on the screen, balances and all, just as you left it.
It's a gut-wrenching moment: the realization that your crypto recovery phrase is gone or, even worse, in someone else's hands. Panic is the natural reaction, but what you do in the next few minutes is absolutely critical. Acting decisively, not desperately, can mean the difference between saving your assets and losing them for good.
This emergency breaks down into two very different scenarios, and each one demands a unique game plan. The first, and by far the most urgent, is when you think your phrase has been stolen or exposed. The second is when your phrase is just lost, but you can still get into your wallet on your phone or computer.

Emergency Plan: What to Do If Your Phrase Is Compromised
If you have even the slightest suspicion that someone else has seen your recovery phrase—maybe you typed it into a sketchy website or found a photo of it in your cloud storage—you have to assume the worst. Your wallet is compromised. A thief with your phrase can drain your funds at any second. It’s now a race against time.
You have one move, and one move only: get your funds out. Now.
- Create a New, Secure Wallet: Grab a trusted device and generate a brand-new wallet. This will give you a completely new recovery phrase. Write it down and get it offline immediately.
- Transfer Everything Out: Go back to your old, compromised wallet and send every last asset to the addresses of your new, secure wallet. Don't wait. Start with your most valuable coins first.
- Abandon the Old Wallet: Once it's empty, consider that wallet radioactive. Never use it again. It is permanently unsafe.
The threat of a stolen seed phrase is no joke. In the first half of 2025 alone, investors lost nearly $3.1 billion to crypto scams and hacks, with recovery phrase theft being a huge contributor. With attacks on personal wallets making up 23.35% of all crypto theft, it's a stark reminder that moving fast is your only defense. You can see more of the chilling data in Ledger's analysis.
What to Do If Your Phrase Is Simply Lost
Losing your recovery phrase—maybe it was destroyed in a fire or you just can’t remember where you put it—is a different kind of problem. If you can still access your funds on an unlocked phone or computer, the situation isn't a five-alarm fire, but it's still incredibly serious. You are one dead battery or software glitch away from losing everything.
You have access to your crypto right now, but you have no backup. Your only priority is to create a new safety net before that access disappears.
The steps are basically the same as the compromised scenario, but the clock isn't ticking quite as loudly, so you can be more methodical.
Create a new wallet, securely back up its new recovery phrase, and then carefully transfer all your assets over. Once that’s done, you can breathe again. Your funds are safe and sound, tied to a new phrase that you control.
But what if the phrase is truly gone and you have no access to any device with your wallet on it? Honestly, the outlook is grim. In most cases, those funds are lost forever. Be extremely skeptical of anyone who promises a guaranteed recovery; many are just scams preying on desperation. While some legitimate professional services might be able to help in very specific, rare situations (like pulling data from a damaged hard drive), their options are severely limited. Always approach them with a healthy dose of caution.
Recovery Phrase FAQs: Your Questions Answered
We've covered a lot of ground, but it's totally normal to still have a few questions buzzing around. Getting comfortable with your crypto recovery phrase is a process, and the details really matter.
Let's tackle some of the most common questions we hear. This section will help button up any loose ends and make sure you're feeling solid about how to protect your crypto.
Can I Change My Crypto Recovery Phrase?
Simply put, no. You can't change the recovery phrase for a wallet that's already in use. Think of the phrase as the master key and the foundation rolled into one; it's the mathematical starting point for all your private keys and is permanently linked to that specific wallet.
If you have any reason to believe your phrase has been compromised, the only safe move is to create a brand-new wallet. This will give you a fresh, secure recovery phrase. From there, you'll need to send all your crypto from the old, compromised wallet to your new one as quickly as you can.
Is a 12-Word Phrase Less Secure Than 24 Words?
While a 24-word phrase is mathematically stronger by a mind-boggling degree, a 12-word phrase is already so secure that it's considered impossible for today's computers to guess. For all practical purposes, both are more than enough to stop a brute-force attack cold.
The real security risk isn't about someone guessing your 12 or 24 words. It's about how you store them. A 24-word phrase scribbled on a sticky note on your monitor is infinitely less secure than a 12-word phrase stamped in steel and locked in a safe.
Your focus should be less on the word count and more on bulletproof, offline storage. That’s where the real security battle is won or lost.
What Happens if I Enter the Words in the Wrong Order?
The order of the words is everything. It's not just a list; it's a precise sequence. If you mix up the order, one of two things will happen:
- You'll get an error. Most wallets are smart enough to know the sequence is invalid and will just stop you in your tracks.
- You'll open a different wallet. In some rare cases, a different sequence of words might actually generate a valid, but completely empty, wallet.
Your funds are only tied to the exact original order. This is why we always recommend numbering the words as you write them down (e.g., 1. apple, 2. river, 3. mountain). It’s a simple step that can save you a world of panic.
Should I Ever Store My Recovery Phrase Digitally?
Never. Not ever. Storing your recovery phrase on any internet-connected device is probably the single biggest mistake you can make. That means no screenshots, no notes apps, no password managers, and definitely no emailing it to yourself.
Any digital file is a sitting duck for hackers, malware, or a clever phishing scam. The gold standard for a reason is to keep your phrase completely offline—etched into metal or written on paper and stored securely. Even better, store it in multiple secure, physical locations.
If you've lost your recovery phrase or are stuck in a tough spot, you don't have to go it alone. Wallet Recovery AI uses specialized, AI-driven techniques to help people get back into their wallets. Find out if our experts can help with your recovery.


Leave a Reply